Chrome NET::ERR_CERT_AUTHORITY_INVALID error on self signing certificate at LocalHost
Categories:
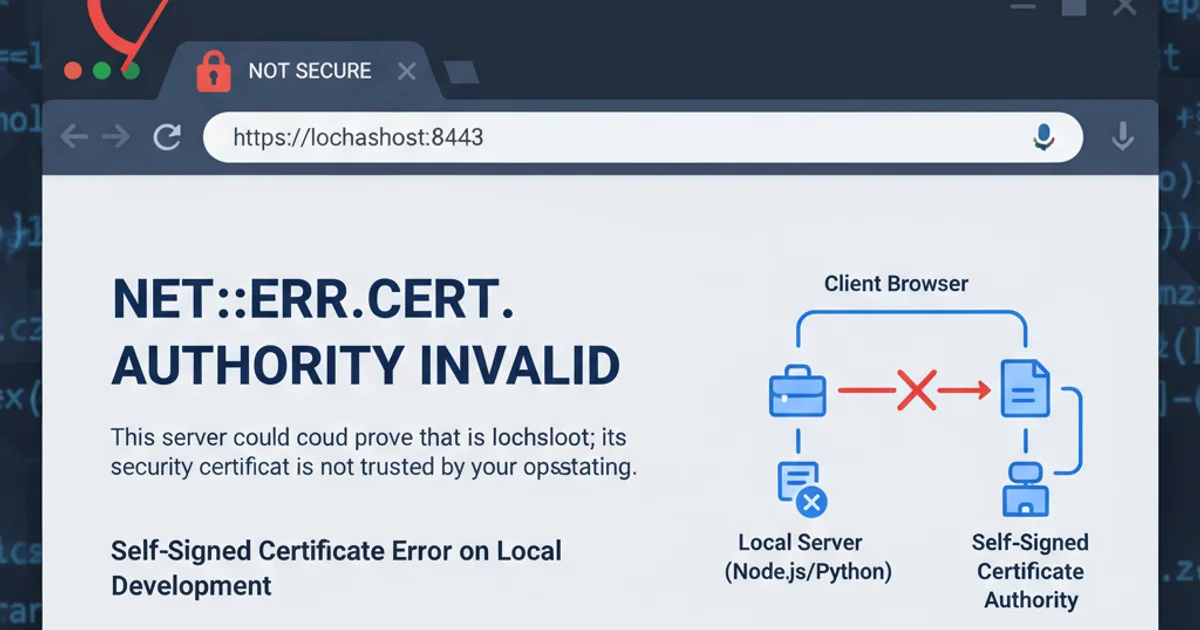
Resolving Chrome's NET::ERR_CERT_AUTHORITY_INVALID for Localhost Self-Signed Certificates
Learn why Chrome flags self-signed certificates on localhost as invalid and discover effective methods to bypass or properly configure your browser for local development.
Developing web applications locally often involves using HTTPS to mimic production environments. This typically requires self-signed SSL certificates. However, Google Chrome, with its stringent security policies, frequently presents a NET::ERR_CERT_AUTHORITY_INVALID error when encountering these certificates. This article explains the root cause of this error and provides practical solutions to ensure a smooth local development workflow without compromising security unnecessarily.
Understanding the NET::ERR_CERT_AUTHORITY_INVALID Error
The NET::ERR_CERT_AUTHORITY_INVALID error indicates that Chrome does not trust the issuer of the SSL certificate presented by your localhost server. In a production environment, certificates are issued by well-known Certificate Authorities (CAs) that are pre-trusted by browsers. Self-signed certificates, by definition, are signed by themselves and are not issued by a recognized CA. Therefore, Chrome, acting as a guardian of your security, flags them as untrusted.
flowchart TD
A[Localhost Server] --> B{Presents Self-Signed Certificate}
B --> C[Chrome Browser]
C --> D{Checks Certificate Trust Chain}
D --> E{"Is Issuer a Trusted CA?"}
E -- No --> F["NET::ERR_CERT_AUTHORITY_INVALID"]
E -- Yes --> G[Secure Connection Established]Flowchart illustrating Chrome's certificate validation process for self-signed certificates.
Common Solutions for Local Development
While the error is a security feature, it can be a hindrance during development. Here are the most common and recommended approaches to resolve it for your localhost setup:
1. Option 1: Trusting the Self-Signed Certificate (Recommended)
The most secure and recommended approach is to explicitly trust your self-signed certificate on your operating system. This involves adding your certificate's root CA to your system's trusted certificate store. Once trusted by the OS, Chrome will also recognize it as valid. This method ensures that only certificates you explicitly trust are accepted, maintaining a good security posture.
2. Option 2: Bypassing Security Warnings (Less Recommended)
For quick, temporary testing, you can sometimes bypass the warning directly in Chrome by clicking 'Proceed to unsafe' or similar options. However, this is not always available for NET::ERR_CERT_AUTHORITY_INVALID and is generally discouraged as it trains users to ignore security warnings. A more persistent, but still less secure, method is to launch Chrome with specific flags, which should only be used for isolated development environments and never for general browsing.
Implementing Certificate Trust on macOS and Windows
The process for trusting a self-signed certificate varies slightly by operating system. Below are general steps for macOS and Windows. You'll first need to generate your self-signed certificate and its corresponding private key. Tools like OpenSSL or mkcert are excellent for this.
macOS
- Generate Certificate: Use
mkcert(recommended) or OpenSSL to create your certificate and key.mkcert -install mkcert localhost 127.0.0.1 ::1mkcertautomatically installs the generated CA into your system's trust store. - Manual Trust (if not using mkcert): Open Keychain Access (Applications > Utilities > Keychain Access).
- Select 'System' keychain on the left, then 'Certificates' category.
- Drag your
.crtfile into the Certificates list. - Double-click the imported certificate, expand the 'Trust' section, and set 'When using this certificate' to 'Always Trust'.
- Close the certificate window and authenticate if prompted.
Windows
- Generate Certificate: Use
mkcert(recommended) or OpenSSL to create your certificate and key.mkcert -install mkcert localhost 127.0.0.1 ::1mkcertautomatically installs the generated CA into your system's trust store. - Manual Trust (if not using mkcert): Open the Microsoft Management Console (MMC) by typing
mmcin the Run dialog (Win+R). - Go to File > Add/Remove Snap-in... > Certificates > Add > Computer account > Local computer > Finish > OK.
- Navigate to Certificates (Local Computer) > Trusted Root Certification Authorities > Certificates.
- Right-click Certificates > All Tasks > Import.
- Follow the Certificate Import Wizard, browsing to your
.crtfile. Place it in the 'Trusted Root Certification Authorities' store. - Complete the wizard.
Using Chrome Flags (Use with Caution)
For very specific, isolated testing scenarios where trusting the certificate is not feasible or desired, you can launch Chrome with flags that relax security. This is highly discouraged for regular use. The most common flag for this issue is --ignore-certificate-errors.
# Windows example
"C:\Program Files\Google\Chrome\Application\chrome.exe" --ignore-certificate-errors --unsafely-treat-insecure-origin-as-secure="https://localhost:8080"
# macOS example
/Applications/Google\ Chrome.app/Contents/MacOS/Google\ Chrome --ignore-certificate-errors --unsafely-treat-insecure-origin-as-secure="https://localhost:8080"
Launching Chrome with security-bypassing flags (replace https://localhost:8080 with your actual development URL).
--ignore-certificate-errors makes your browser vulnerable to man-in-the-middle attacks. Only use this flag in a completely isolated development environment and close the browser instance immediately after testing. Never use it for general web browsing.By understanding the security implications and choosing the appropriate method, you can effectively manage NET::ERR_CERT_AUTHORITY_INVALID errors for your localhost development, ensuring a productive and secure workflow.