Does typekit pose a security risk?
Categories:
Does Typekit Pose a Security Risk to Your Website?

Explore the security implications of using Typekit (now Adobe Fonts) and understand best practices to mitigate potential risks.
Typekit, now integrated into Adobe Fonts, is a popular service that allows web developers to use a wide variety of high-quality fonts on their websites. While it offers significant aesthetic and functional benefits, the use of any third-party service on your website inevitably introduces potential security considerations. This article delves into the common security concerns associated with using Typekit/Adobe Fonts and provides guidance on how to ensure your implementation is as secure as possible.
Understanding the Core Security Concerns
The primary security concerns with Typekit stem from its nature as a third-party resource loaded onto your website. When a user visits your site, their browser makes a request to Adobe's servers to fetch the fonts. This process introduces several vectors for potential issues, though it's important to note that Adobe has robust security measures in place.
sequenceDiagram
participant UserBrowser as User's Browser
participant YourWebsite as Your Website Server
participant AdobeFonts as Adobe Fonts Server
UserBrowser->>YourWebsite: Request HTML/CSS
YourWebsite-->>UserBrowser: Send HTML/CSS (with font references)
UserBrowser->>AdobeFonts: Request Font Files (e.g., WOFF2)
AdobeFonts-->>UserBrowser: Send Font Files
UserBrowser->>UserBrowser: Render Page with Custom FontsSequence diagram illustrating how a user's browser loads fonts from Adobe Fonts.
The main concerns typically revolve around:
- Supply Chain Attacks: If Adobe's servers were compromised, malicious code could potentially be injected into the font files or the JavaScript used to load them, affecting all websites using the service.
- Privacy Concerns: Loading fonts from a third-party server means that Adobe receives information about your users' requests (IP address, user agent, referrer, etc.). While Adobe states they do not use this data to build profiles of users, it's a data point to consider.
- Availability and Performance: While not strictly a security risk, reliance on an external service means your site's appearance depends on Adobe's servers being available and responsive. An outage could lead to your site displaying fallback fonts, impacting user experience.
- Cross-Site Scripting (XSS) via Font Loading JavaScript: Less common, but theoretically, if the JavaScript provided by Typekit for font loading were compromised, it could lead to XSS vulnerabilities.
Mitigating Security Risks with Typekit/Adobe Fonts
While no system is entirely risk-free, several best practices can significantly reduce the potential security exposure when using Typekit or any other third-party font service.
1. Implement a Robust Content Security Policy (CSP)
A Content Security Policy is a crucial security layer that helps mitigate XSS and other code injection attacks. By defining a strict CSP, you can tell the browser exactly which domains are allowed to serve scripts, stylesheets, images, and fonts. For Typekit/Adobe Fonts, you'll need to allow connections to their domains for fonts and potentially scripts.
Here's an example of relevant CSP directives:
Content-Security-Policy: default-src 'self';
script-src 'self' https://use.typekit.net;
style-src 'self' https://use.typekit.net;
font-src 'self' https://use.typekit.net;
Example CSP directives for allowing Typekit/Adobe Fonts.
This CSP example allows scripts, styles, and fonts only from your own domain ('self') and from https://use.typekit.net. Adjust default-src and other directives as needed for your specific site.
2. Use Subresource Integrity (SRI) for JavaScript (Where Applicable)
Subresource Integrity (SRI) allows browsers to verify that resources they fetch (like scripts or stylesheets) have not been tampered with. While Adobe Fonts primarily delivers fonts, they also provide a small JavaScript snippet to load the fonts asynchronously. If you're embedding this script directly, you might be able to use SRI, though it's more commonly applied to CDN-hosted libraries like jQuery.
Adobe Fonts' dynamic nature (font files can change) makes SRI for the font files themselves impractical. However, for the initial loading script, if you're hosting it or referencing a static version, SRI could be considered. Always check Adobe's documentation for the most current and recommended integration methods.
3. Monitor and Audit Third-Party Resources
Regularly review all third-party resources loaded on your website. This includes not just Typekit, but analytics scripts, advertising networks, and other external services. Tools like browser developer consoles, web security scanners, and network monitoring can help identify unexpected resource loads or suspicious activity.
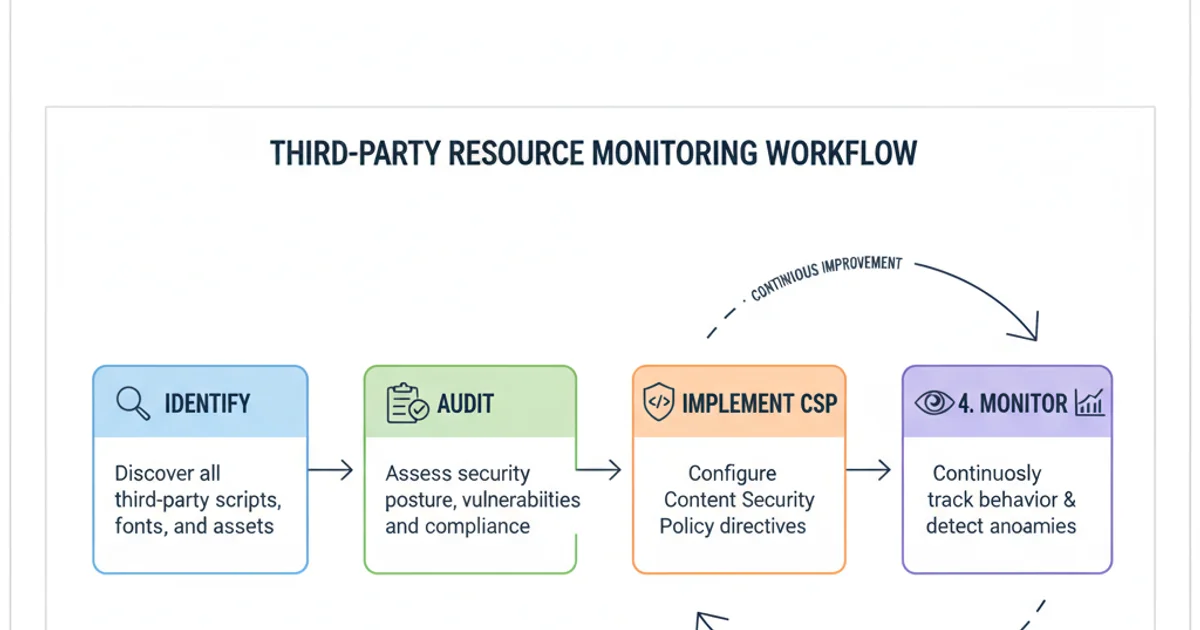
A workflow for continuous monitoring of third-party resources.
4. Consider Self-Hosting (with caveats)
For extreme security requirements or to eliminate third-party dependencies entirely, some organizations choose to self-host their fonts. However, this is generally not an option for Typekit/Adobe Fonts due to licensing restrictions. Adobe Fonts are licensed for use via their service, not for direct download and self-hosting. Attempting to self-host Typekit fonts would violate their terms of service and potentially copyright law.
If self-hosting is a critical requirement, you would need to purchase font licenses directly from font foundries that permit self-hosting and then manage the font files yourself, including optimizing them for web use.