How can someone get the BSSID of a router without connecting to it?
Categories:
Unveiling the Hidden: How to Find a Router's BSSID Without Connecting

Discover various techniques and tools to identify a Wi-Fi router's BSSID (Basic Service Set Identifier) without needing to establish a connection, crucial for network analysis and security assessments.
The BSSID (Basic Service Set Identifier) is a unique MAC address that identifies a wireless access point (AP) or router. While the SSID (Service Set Identifier) is the human-readable name of a Wi-Fi network, the BSSID is its machine-readable identifier. Understanding how to obtain a BSSID without connecting to the network is invaluable for network administrators, security professionals, and anyone interested in wireless network analysis. This article explores several methods, ranging from built-in operating system tools to specialized third-party software, to help you uncover this crucial piece of network information.
Understanding BSSID and Its Importance
Before diving into the methods, let's clarify what a BSSID is and why it matters. Every Wi-Fi access point broadcasts its presence, and part of that broadcast includes its BSSID. In most cases, the BSSID is simply the MAC address of the wireless interface on the router or access point. When a router broadcasts multiple SSIDs (e.g., a 2.4 GHz and a 5 GHz network), each SSID will typically have a unique BSSID, even if they originate from the same physical device.
Knowing the BSSID is important for several reasons:
- Network Troubleshooting: It helps differentiate between multiple access points with the same SSID (e.g., in a large office or apartment building).
- Security Auditing: For penetration testing or security assessments, identifying BSSIDs is a fundamental step in mapping out a target network's infrastructure.
- Location Tracking: BSSIDs are often used in Wi-Fi positioning systems (WPS) to determine a device's location.
- Forensics: In incident response, BSSIDs can help trace the path of a compromised device or identify rogue access points.
flowchart TD
A[Wireless Router] --> B{Broadcasts Beacons}
B --> C[Contains SSID & BSSID]
C --> D[Client Device (e.g., Laptop, Phone)]
D --> E{Scans for Networks}
E --> F[Receives Beacons]
F --> G[Extracts SSID & BSSID]
G --> H[Displays Available Networks]
H --> I{User Selects Network}
I --> J[Connects to BSSID]Simplified flow of BSSID discovery and connection
Methods for BSSID Discovery
There are several effective ways to discover a router's BSSID without actively connecting to its network. These methods rely on passively listening to the Wi-Fi beacon frames that all access points broadcast.
1. Using Operating System Tools
Most modern operating systems provide command-line tools that can scan for Wi-Fi networks and display detailed information, including BSSIDs.
Windows (Command Prompt/PowerShell)
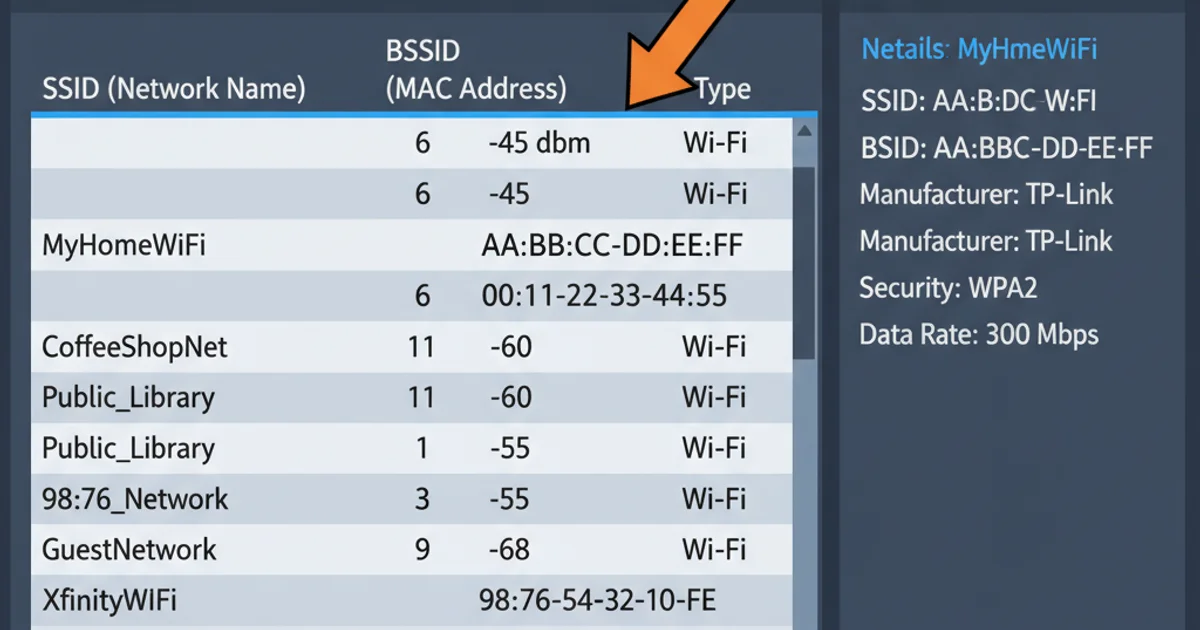
On Windows, you can use the netsh wlan show networks mode=bssid command. This command lists all visible wireless networks and their associated BSSIDs.
netsh wlan show networks mode=bssid
This will output a list similar to this:
Interface name: Wi-Fi
There are 2 networks currently visible.
SSID 1 : MyHomeNetwork
Network type : Infrastructure
Authentication : WPA2-Personal
Encryption : CCMP
BSSID 1 : 00:11:22:33:44:55
Signal : 90%
Radio type : 802.11n
Channel : 6
Basic rates (Mbps) : 1 2 5.5 11
Other rates (Mbps) : 6 9 12 18 24 36 48 54
SSID 2 : Public_WiFi
Network type : Infrastructure
Authentication : Open
Encryption : None
BSSID 1 : AA:BB:CC:DD:EE:FF
Signal : 65%
Radio type : 802.11ac
Channel : 149
Basic rates (Mbps) : 6 12 24
Other rates (Mbps) : 9 18 36 48 54
macOS (Airport Utility)
macOS users can leverage the built-in airport utility, which is usually located at /System/Library/PrivateFrameworks/Apple80211.framework/Versions/A/Resources/airport. To use it, you might need to specify the full path or create an alias.
/System/Library/PrivateFrameworks/Apple80211.framework/Versions/A/Resources/airport -s
This command provides a list of SSIDs, BSSIDs, signal strength, and channel information.
SSID BSSID RSSI CHANNEL HT CC SECURITY (auth/unicast/group)
MyHomeNetwork 00:11:22:33:44:55 -50 1,+1 Y -- WPA2(PSK/AES/AES)
Public_WiFi AA:BB:CC:DD:EE:FF -70 149 Y -- WPA2(PSK/AES/AES)
Linux (iw, iwlist)
Linux offers powerful tools like iw and iwlist for wireless network scanning. iw is generally preferred for modern systems.
Using iw:
sudo iw dev wlan0 scan | grep -E "SSID|BSSID"
Replace wlan0 with your wireless interface name (you can find it using iw dev).
Example output:
BSS 00:11:22:33:44:55 (on wlan0)
SSID: MyHomeNetwork
BSS AA:BB:CC:DD:EE:FF (on wlan0)
SSID: Public_WiFi
Using iwlist (older method, might require root):
sudo iwlist wlan0 scan | grep -E "ESSID|Address"
Example output:
Cell 01 - Address: 00:11:22:33:44:55
ESSID:"MyHomeNetwork"
Cell 02 - Address: AA:BB:CC:DD:EE:FF
ESSID:"Public_WiFi"
iw dev wlan0 scan usually works in managed mode for basic BSSID discovery.2. Specialized Wireless Scanning Tools
For more in-depth analysis and a richer user experience, dedicated wireless scanning tools are highly recommended. These tools often provide real-time updates, graphical interfaces, and additional network details.
Kismet displaying various Wi-Fi networks and their BSSIDs.
Kismet Wireless
Kismet is a powerful network detector, sniffer, and intrusion detection system. It works by passively collecting packets and detecting networks, including hidden ones, without sending any packets itself. Kismet is particularly effective for identifying BSSIDs, even for networks that don't broadcast their SSIDs.
Key Features:
- Passive sniffing (doesn't connect or interact with APs).
- Detects hidden networks.
- Identifies BSSIDs, SSIDs, channels, encryption types, and client devices.
- Supports various wireless cards and operating systems (primarily Linux).
How to use Kismet (basic steps):
- Install Kismet (e.g.,
sudo apt install kismeton Debian/Ubuntu). - Ensure your wireless card supports monitor mode.
- Start Kismet (often
sudo kismetorkismetafter configuration). - Kismet will automatically start scanning and display detected networks with their BSSIDs.
Wireshark
While primarily a packet analyzer, Wireshark can be used to capture Wi-Fi traffic in monitor mode and then filter for beacon frames to extract BSSIDs. This method is more involved but provides the most granular control and detail.
How to use Wireshark for BSSID discovery:
- Put your wireless adapter into monitor mode (e.g.,
sudo airmon-ng start wlan0on Linux). - Start Wireshark and select your monitor-mode interface.
- Apply a display filter for beacon frames:
wlan.fc.type_subtype == 0x08 - Look for the 'Source' MAC address in the captured beacon frames; this is the BSSID.
sudo on Linux) and a compatible wireless card. Always ensure you have permission to scan networks in your vicinity.3. Mobile Applications
For quick on-the-go BSSID discovery, several mobile applications are available for both Android and iOS that can scan for Wi-Fi networks and display their BSSIDs.
Android Apps
Apps like "WiFi Analyzer" (by farproc or similar) are popular choices. They provide a graphical representation of surrounding Wi-Fi networks, including their SSIDs, BSSIDs, signal strength, and channel usage. These apps are user-friendly and require no special setup beyond installation.
iOS Apps
iOS has stricter limitations on accessing raw Wi-Fi information for third-party apps. While some apps might show basic network details, obtaining BSSIDs directly from third-party apps can be challenging due to Apple's security policies. However, Apple's own "AirPort Utility" app (when used with an AirPort Base Station) can provide some network details, and for general scanning, you might find limited information. For more comprehensive data, a computer-based solution is usually necessary.
By utilizing these methods, you can effectively discover the BSSID of a router without needing to connect to its network, providing valuable insights for network management, security, and troubleshooting.