CookieParser vs req.cookies expressjs
Categories:
CookieParser vs. req.cookies in Express.js: Understanding Cookie Handling
Explore the roles of the cookie-parser middleware and the req.cookies object in Express.js for managing HTTP cookies.
When building web applications with Express.js, handling HTTP cookies is a common requirement for managing user sessions, preferences, and other stateful information. Express.js provides mechanisms to interact with cookies, but understanding the roles of the cookie-parser middleware and the req.cookies object is crucial for effective implementation. This article will demystify their functions, show you how to use them, and highlight best practices for secure cookie management.
The Role of cookie-parser Middleware
The cookie-parser is a popular middleware for Express.js that parses incoming HTTP request headers and populates req.cookies with an object keyed by cookie names. Without this middleware, req.cookies would be undefined. It's essential for any application that needs to read cookies sent by the client.
Historically, cookie-parser was part of Express.js itself, but it was later extracted into a separate module to keep the core framework lean. While still widely used, modern Express versions (4.x and above) often recommend using express-session or similar session management libraries that might internally handle cookie parsing, or even express.json() and express.urlencoded() for body parsing, but cookie-parser remains the go-to for simply parsing raw Cookie headers.
const express = require('express');
const cookieParser = require('cookie-parser');
const app = express();
// Use cookie-parser middleware
app.use(cookieParser());
app.get('/', (req, res) => {
// Access parsed cookies
console.log('Cookies:', req.cookies);
// Set a new cookie
res.cookie('myCookie', 'myValue', { maxAge: 900000, httpOnly: true });
res.send('Hello World! Check your cookies.');
});
app.listen(3000, () => {
console.log('Server listening on port 3000');
});
Basic Express.js application using cookie-parser
sequenceDiagram
participant Client
participant ExpressApp
participant CookieParser
Client->>ExpressApp: HTTP Request (with 'Cookie' header)
ExpressApp->>CookieParser: Pass request to middleware
CookieParser->>ExpressApp: Parse 'Cookie' header, populate req.cookies
ExpressApp->>ExpressApp: Route handler executes
ExpressApp->>Client: HTTP Response (with 'Set-Cookie' header)Sequence of cookie parsing with cookie-parser
Understanding req.cookies
The req.cookies object is a property added to the request object by the cookie-parser middleware. It's an object where keys are the names of the cookies sent by the client, and values are their corresponding string values. This object provides a convenient way to access client-sent cookies within your route handlers.
It's important to note that req.cookies only contains cookies that were sent by the client in the Cookie HTTP header. It does not contain cookies that you might have just set on the res object using res.cookie(). Those cookies will only be available in req.cookies on subsequent requests from the client, after the client has received and stored them.
app.get('/read-cookie', (req, res) => {
const userPreference = req.cookies.userPref;
if (userPreference) {
res.send(`Your preference is: ${userPreference}`);
} else {
res.send('No user preference cookie found.');
}
});
app.get('/set-cookie', (req, res) => {
res.cookie('userPref', 'darkTheme', { maxAge: 3600000, httpOnly: true });
res.send('User preference cookie set. Refresh to see it.');
});
app.get('/clear-cookie', (req, res) => {
res.clearCookie('userPref');
res.send('User preference cookie cleared.');
});
Examples of reading, setting, and clearing cookies using req.cookies and res.cookie()
cookie-parser also provides req.signedCookies. You'll need to pass a secret string to cookieParser() to enable this feature, which helps prevent tampering.Best Practices for Cookie Management
When working with cookies, security and proper management are paramount. Here are some best practices:
httpOnlyFlag: Always set thehttpOnlyflag totruefor sensitive cookies (like session IDs). This prevents client-side JavaScript from accessing the cookie, mitigating XSS attacks.secureFlag: For applications served over HTTPS, set thesecureflag totrue. This ensures the cookie is only sent over encrypted connections.SameSiteAttribute: Use theSameSiteattribute (Lax,Strict, orNone) to control when cookies are sent with cross-site requests, helping to prevent CSRF attacks.- Expiration: Set appropriate
maxAgeorexpiresfor cookies. Avoid excessively long expiration times for sensitive data. - Signed Cookies: Use signed cookies (with
cookie-parser's secret) to detect if a cookie has been tampered with by the client. Note that signing only prevents tampering, not reading. - Avoid Storing Sensitive Data: Never store highly sensitive information (e.g., passwords, credit card numbers) directly in cookies. Instead, store a session ID in the cookie and keep sensitive data on the server-side, linked to that session ID.
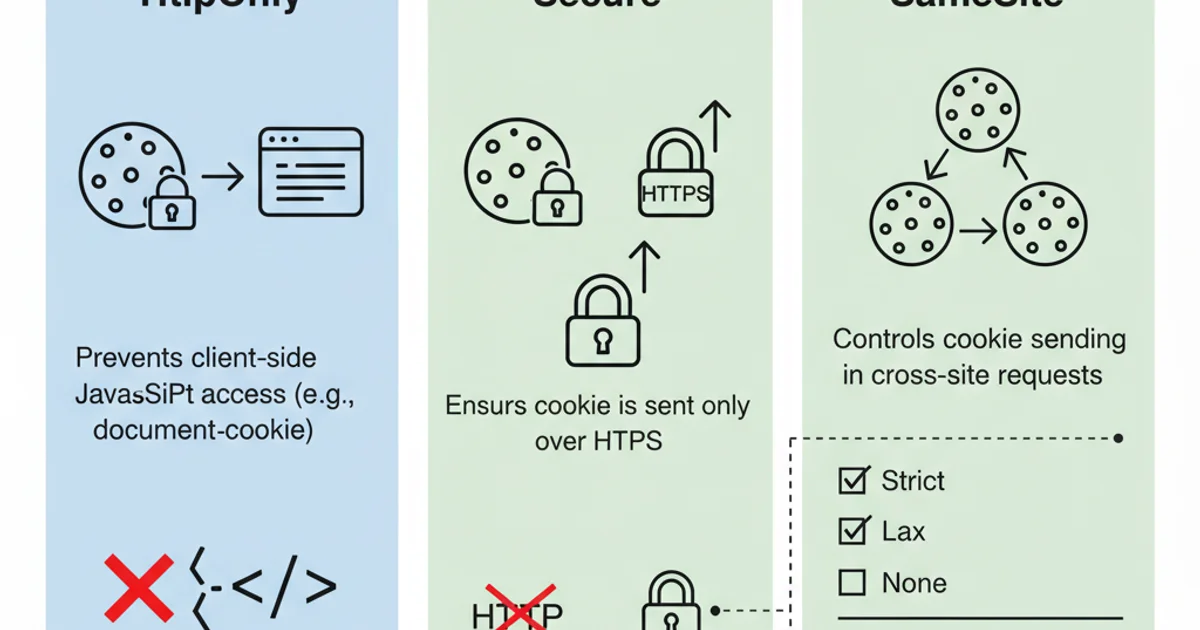
Key security attributes for HTTP cookies
cookie-parser is great for simple cookie parsing, for robust session management, consider using dedicated session middleware like express-session, which often integrates cookie parsing and signing more comprehensively.