Is there a way to make Firefox ignore invalid ssl-certificates?
Categories:
Bypassing SSL/TLS Certificate Validation in Firefox for Debugging
Learn how to configure Firefox to temporarily ignore invalid SSL/TLS certificates, a common requirement for debugging local development environments or testing specific network conditions.
When developing web applications, especially those interacting with local servers or custom APIs, you often encounter self-signed or otherwise invalid SSL/TLS certificates. By default, Firefox, like other modern browsers, prioritizes security and will block access to sites with such certificates, displaying a 'Secure Connection Failed' error. While this is crucial for general browsing safety, it can be a significant hurdle during development and testing. This article will guide you through the methods to temporarily bypass these warnings in Firefox, enabling you to proceed with your debugging tasks.
Understanding SSL/TLS Certificate Warnings
SSL/TLS certificates are fundamental to secure communication over the internet. They verify the identity of a website and encrypt data exchanged between your browser and the server. When Firefox encounters an invalid certificate, it means one or more of these conditions are not met:
- Untrusted Issuer: The certificate is self-signed or issued by a Certificate Authority (CA) not recognized by your browser.
- Expired or Not Yet Valid: The certificate's validity period has passed or has not yet begun.
- Hostname Mismatch: The domain name in the certificate does not match the website's actual domain.
- Revoked Certificate: The certificate has been explicitly revoked by its issuer.
For production environments, these warnings are critical indicators of potential security risks. However, in a controlled development environment, they are often expected and can be safely bypassed for specific debugging purposes.
flowchart TD
A[User Navigates to HTTPS Site] --> B{Firefox Checks Certificate Validity}
B -->|Valid| C[Secure Connection Established]
B -->|Invalid| D[Display 'Secure Connection Failed' Error]
D --> E{User Action?}
E -->|Accept Risk (Dev Only)| F[Bypass Warning]
E -->|Do Not Proceed| G[Block Access]
F --> CFirefox SSL/TLS Certificate Validation Flow
Method 1: Temporarily Accepting the Risk (Per-Site)
This is the most common and generally recommended approach for development. When you encounter a certificate error, Firefox usually provides an option to proceed. This method allows you to bypass the warning for a specific site and session, or permanently add an exception for that site.
1. Access the problematic site
Navigate to the HTTPS URL that is presenting the invalid certificate.
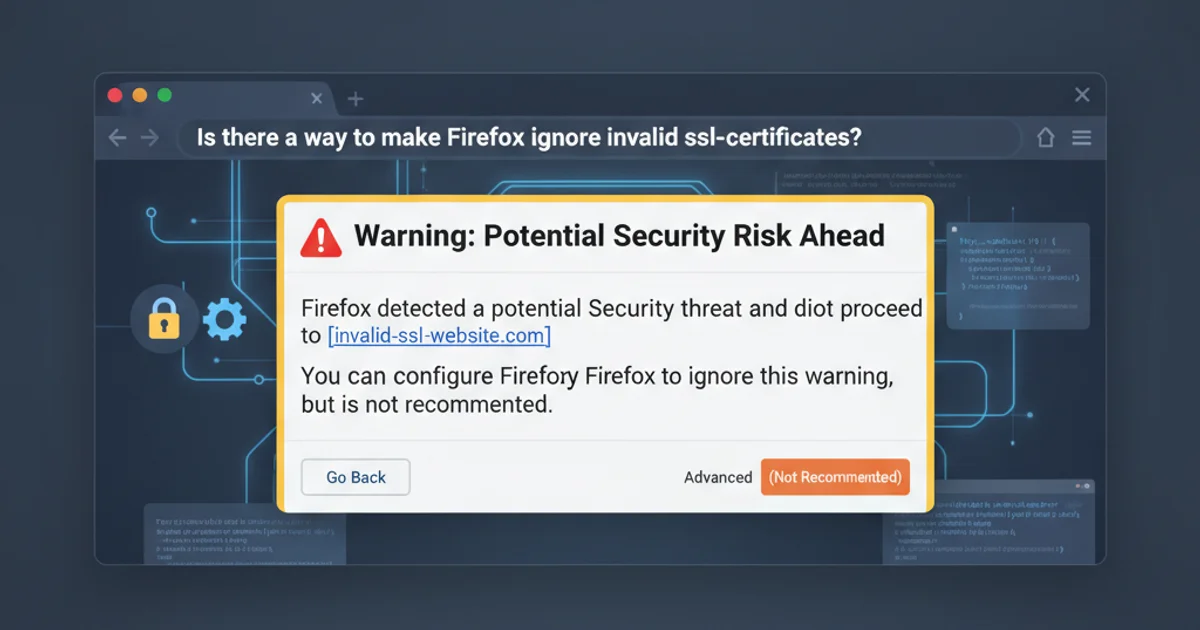
2. Identify the error page
Firefox will display a 'Secure Connection Failed' or 'Warning: Potential Security Risk Ahead' page.
3. View Advanced Options
Click the 'Advanced...' button on the error page. This will reveal more details about the certificate issue and options to proceed.
4. Accept the Risk and Continue
Click 'Accept the Risk and Continue'. This will add a temporary exception for the current session. For some errors, you might see an 'Add Exception...' button which allows you to permanently store the exception for that specific certificate.
Method 2: Disabling Certificate Validation (Advanced/Not Recommended)
While not generally recommended for regular use, there are advanced settings in Firefox's about:config that can disable certain aspects of SSL/TLS validation. This should only be used as a last resort for very specific debugging scenarios and always reverted afterward.
1. Open about:config
Type about:config into the Firefox address bar and press Enter. Accept the warning about voiding your warranty.
2. Search for security preferences
In the search bar, type security.enterprise_roots.enabled.
3. Toggle the preference
Double-click the security.enterprise_roots.enabled preference to toggle its value to true. This allows Firefox to trust certificates installed in the operating system's certificate store. While not directly disabling validation, it can help with corporate proxies or custom CAs.
4. Search for security.tls.insecure_fallback_hosts
This preference allows you to specify a comma-separated list of hostnames for which Firefox will allow insecure TLS fallbacks. This is highly insecure and should be used with extreme caution.
5. Search for security.ssl.enable_ocsp_stapling
Setting this to false disables OCSP stapling, which is a mechanism for checking certificate revocation status. This is generally not recommended as it reduces security.
about:config preferences, especially those related to security, can severely compromise your browser's security. Only make changes if you fully understand the implications and revert them immediately after your debugging session. It's generally safer to use Method 1 or import the certificate into your system's trust store.Method 3: Importing the Certificate into Your Trust Store
For a more robust and slightly more secure development workflow, you can import your self-signed certificate into your operating system's or Firefox's own certificate trust store. This tells Firefox to explicitly trust that specific certificate, treating it as valid without needing to accept risks every time.
1. Export the certificate
If you generated a self-signed certificate, ensure you have access to its .crt or .pem file. If you're encountering an error on a server you control, you might be able to download the certificate from the browser's error page (look for 'View Certificate' or similar options).
2. Open Firefox Certificate Manager
Go to Firefox Settings -> Privacy & Security -> Scroll down to Certificates and click View Certificates....
3. Import the certificate
In the 'Certificate Manager' window, go to the 'Authorities' tab. Click 'Import...' and select your certificate file. When prompted, check the box(es) to 'Trust this CA to identify websites' and click 'OK'.