UDP/TCP hole punching vs UPnP vs STUN vs?
Categories:
Navigating NAT: UDP/TCP Hole Punching vs. UPnP vs. STUN
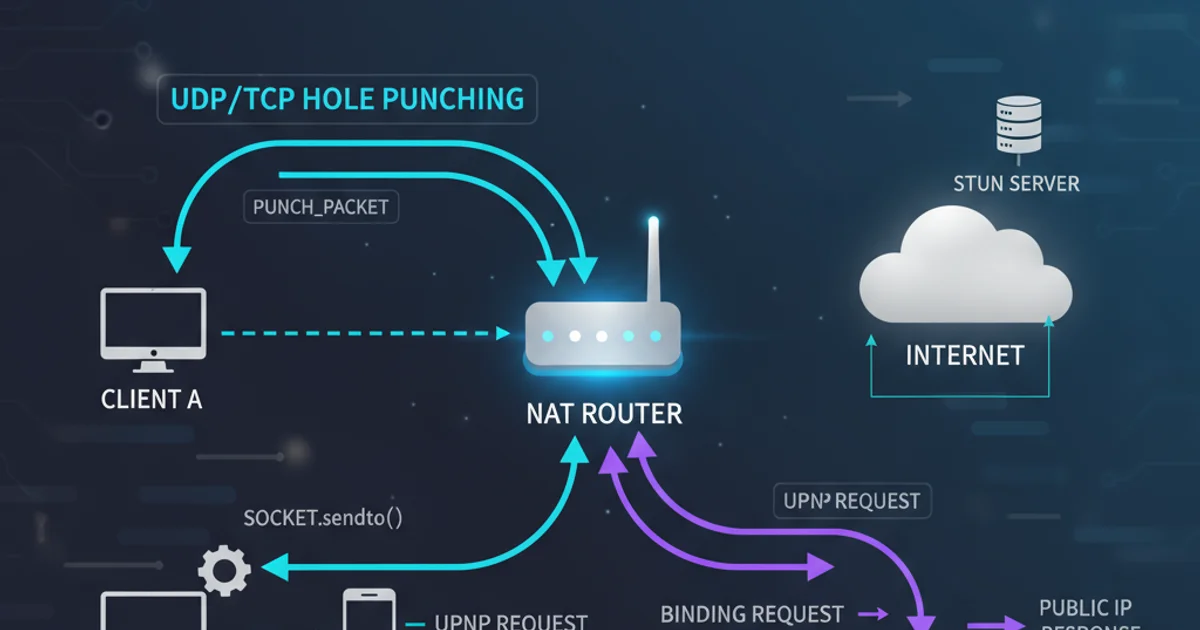
Explore the challenges of network address translation (NAT) and compare common techniques like hole punching, UPnP, and STUN for establishing direct peer-to-peer connections.
In today's interconnected world, many applications rely on direct communication between clients, often referred to as peer-to-peer (P2P) connections. However, the widespread use of Network Address Translators (NATs) poses a significant challenge to establishing these direct links. NATs modify network address information in packet headers while in transit across a router, primarily to conserve public IP addresses and enhance security. This article delves into the common strategies used to overcome NAT restrictions, including UDP/TCP hole punching, UPnP, and STUN, helping you understand their mechanisms, advantages, and limitations.
The NAT Problem: Why Direct Connections Are Hard
A NAT device sits between a private network and the public internet. It maps multiple private IP addresses to a single public IP address. When an internal client initiates an outbound connection, the NAT rewrites the source IP and port of the packet to its own public IP and an available public port. It then maintains a mapping table to route incoming response packets back to the correct internal client. The problem arises when an external client tries to initiate a connection to an internal client; the NAT has no prior mapping for this unsolicited incoming traffic and typically drops the packets, preventing direct communication.
flowchart TD
subgraph Private Network
ClientA[Client A (192.168.1.10:5000)]
end
Router[NAT Router (Public IP: 203.0.113.1)]
Internet[Internet]
ClientB[Client B (External IP: 198.51.100.5:6000)]
ClientA -- Outbound Request --> Router
Router -- Rewrites Source (203.0.113.1:12345) --> Internet
Internet -- Inbound Unsolicited --> Router
Router -- X Drops Packet X --> ClientA
style ClientA fill:#bbf,stroke:#333,stroke-width:2px
style ClientB fill:#bbf,stroke:#333,stroke-width:2px
style Router fill:#f9f,stroke:#333,stroke-width:2px
style Internet fill:#ccc,stroke:#333,stroke-width:2pxHow NAT blocks unsolicited incoming connections.
UDP/TCP Hole Punching: The Art of Simultaneous Connections
Hole punching is a technique that leverages the behavior of most NATs to establish direct P2P connections. The core idea is that if two clients behind different NATs (or one behind a NAT and one on the public internet) simultaneously attempt to connect to each other, their respective NATs will create temporary mappings (holes) in their firewall rules. When the packets from one client arrive at the other client's NAT, they match the recently created 'hole' and are allowed through. This requires a third-party server, often called a 'rendezvous server,' to coordinate the exchange of public IP and port information between the peers.
sequenceDiagram
participant ClientA
participant NAT_A
participant RendezvousServer
participant NAT_B
participant ClientB
ClientA->>RendezvousServer: Register private IP/port
ClientB->>RendezvousServer: Register private IP/port
RendezvousServer-->>ClientA: Client B's public/private IP/port
RendezvousServer-->>ClientB: Client A's public/private IP/port
ClientA->>NAT_A: Send UDP/TCP packet to Client B's public IP/port
NAT_A->>Internet: Create outbound mapping (hole)
ClientB->>NAT_B: Send UDP/TCP packet to Client A's public IP/port
NAT_B->>Internet: Create outbound mapping (hole)
Internet->>NAT_B: Client A's packet arrives
NAT_B-->>ClientB: Packet forwarded (matches hole)
Internet->>NAT_A: Client B's packet arrives
NAT_A-->>ClientA: Packet forwarded (matches hole)
ClientA<->>ClientB: Direct P2P connection establishedUDP/TCP Hole Punching sequence for establishing a direct connection.
UPnP (Universal Plug and Play): Router Configuration on Demand
UPnP is a set of networking protocols that allows devices on a local network to discover each other and establish functional network services for data sharing, communications, and entertainment. For NAT traversal, UPnP enables applications to automatically configure port forwarding rules on the router. Instead of relying on a rendezvous server and simultaneous connections, an application can directly ask the UPnP-enabled router to open a specific port and forward incoming traffic to its internal IP address and port. This effectively bypasses the NAT's blocking behavior for that specific port.
sequenceDiagram
participant Client
participant UPnP_Router
participant ExternalClient
Client->>UPnP_Router: Discover UPnP services
UPnP_Router-->>Client: UPnP service available
Client->>UPnP_Router: Request port mapping (e.g., external port 12345 to internal 5000)
UPnP_Router-->>Client: Port mapping successful
ExternalClient->>UPnP_Router: Connect to Public IP:12345
UPnP_Router-->>Client: Forward connection to Internal IP:5000
Client<->>ExternalClient: Direct connection establishedUPnP port mapping process for direct access.
STUN (Session Traversal Utilities for NAT): Discovering Your Public Identity
STUN is a protocol designed to allow a client behind a NAT to discover its public IP address and the type of NAT it is behind. A STUN server, located on the public internet, responds to requests from clients with their public IP address and the port that the NAT used for the outbound connection. This information is crucial for hole punching, as peers need to know each other's public endpoints to attempt direct connections. STUN itself does not establish connections; it merely provides the necessary information for other techniques like hole punching to work.
sequenceDiagram
participant Client
participant NAT
participant STUN_Server
Client->>NAT: Send STUN Binding Request (to STUN Server)
NAT->>STUN_Server: Forward STUN Binding Request (rewrites source IP/port)
STUN_Server-->>NAT: STUN Binding Response (contains NAT's public IP/port)
NAT-->>Client: Forward STUN Binding Response
Client->>Client: Learns its public IP and port from STUN responseSTUN protocol for discovering public IP and port.
Comparison and When to Use Each
Each NAT traversal technique has its strengths and weaknesses, making them suitable for different scenarios. Understanding these differences is key to choosing the right approach for your application.
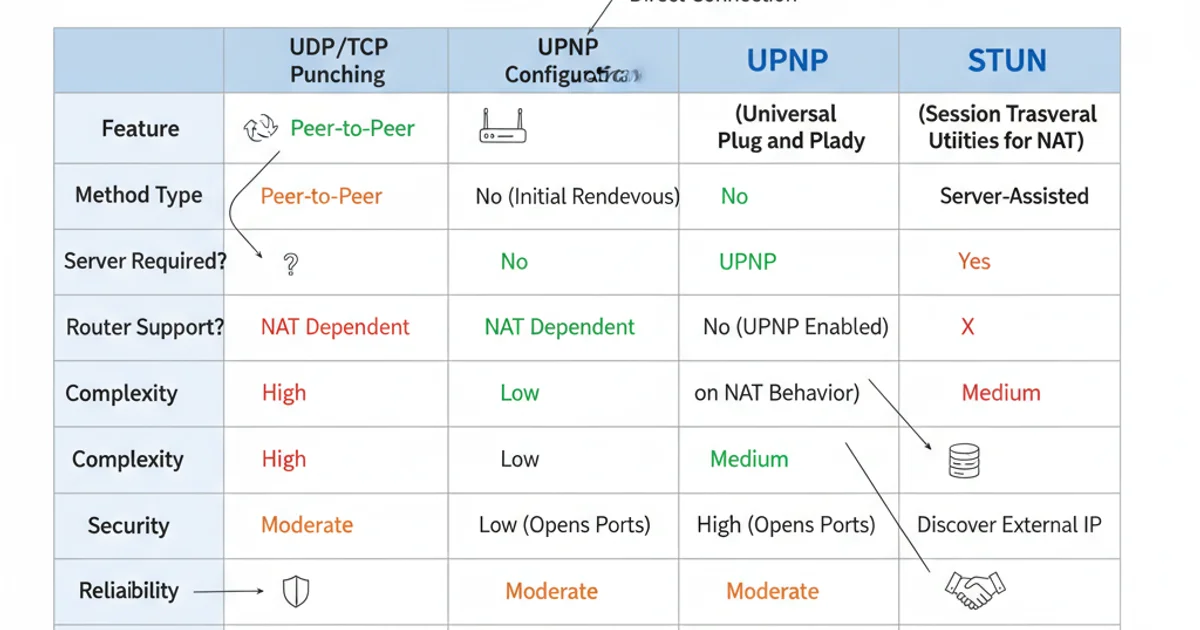
Comparison of NAT traversal techniques.
In summary:
- STUN is foundational. It helps clients discover their public IP and NAT type, which is often a prerequisite for hole punching.
- UDP/TCP Hole Punching is a robust and widely used technique for P2P applications, especially when UPnP is unavailable or disabled. It's generally preferred for its reliability and security over UPnP.
- UPnP offers the simplest setup for end-users but comes with significant security implications. It's often used in consumer-grade devices and applications where ease of use outweighs security concerns, or within trusted local networks.