Generate a key for AES
Categories:
Generating Secure AES Keys in Java

Learn how to generate strong and cryptographically secure Advanced Encryption Standard (AES) keys in Java for robust data encryption.
Advanced Encryption Standard (AES) is one of the most widely used and secure symmetric encryption algorithms available today. To effectively use AES for encrypting and decrypting sensitive data, you need a strong, randomly generated secret key. This article will guide you through the process of generating cryptographically secure AES keys in Java, covering different key sizes and best practices.
Understanding AES Key Requirements
AES operates with key sizes of 128, 192, or 256 bits. The strength of your encryption directly correlates with the key size; a larger key size offers greater security but also slightly increases computational overhead. For most modern applications, AES-256 is recommended, providing a very high level of security against brute-force attacks. It's crucial that these keys are generated using a cryptographically strong pseudo-random number generator (CSPRNG) to prevent predictability and ensure their randomness.
flowchart TD
A[Start Key Generation] --> B{Choose Key Size (128, 192, 256 bits)}
B --> C[Initialize KeyGenerator for AES]
C --> D[Initialize KeyGenerator with SecureRandom and Key Size]
D --> E[Generate SecretKey]
E --> F[Store/Use SecretKey Securely]
F --> G[End Key Generation]Flowchart for AES Key Generation Process
Generating AES Keys with KeyGenerator
Java's javax.crypto.KeyGenerator class is the standard way to generate symmetric keys. It abstracts away the complexities of cryptographic randomness and ensures that the generated keys are suitable for the specified algorithm. You instantiate KeyGenerator for the "AES" algorithm and then initialize it with a SecureRandom instance and the desired key size.
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
import java.security.NoSuchAlgorithmException;
import java.security.SecureRandom;
public class AesKeyGenerator {
public static SecretKey generateAesKey(int keySizeBits) throws NoSuchAlgorithmException {
if (keySizeBits != 128 && keySizeBits != 192 && keySizeBits != 256) {
throw new IllegalArgumentException("Invalid AES key size. Must be 128, 192, or 256 bits.");
}
KeyGenerator keyGen = KeyGenerator.getInstance("AES");
SecureRandom secureRandom = new SecureRandom(); // Uses OS-provided randomness
keyGen.init(keySizeBits, secureRandom);
return keyGen.generateKey();
}
public static void main(String[] args) {
try {
// Generate a 256-bit AES key
SecretKey aesKey256 = generateAesKey(256);
System.out.println("Generated AES-256 Key Algorithm: " + aesKey256.getAlgorithm());
System.out.println("Generated AES-256 Key Format: " + aesKey256.getFormat());
System.out.println("Generated AES-256 Key Length (bytes): " + aesKey256.getEncoded().length);
// Generate a 128-bit AES key
SecretKey aesKey128 = generateAesKey(128);
System.out.println("\nGenerated AES-128 Key Algorithm: " + aesKey128.getAlgorithm());
System.out.println("Generated AES-128 Key Format: " + aesKey128.getFormat());
System.out.println("Generated AES-128 Key Length (bytes): " + aesKey128.getEncoded().length);
} catch (NoSuchAlgorithmException e) {
System.err.println("AES algorithm not found: " + e.getMessage());
} catch (IllegalArgumentException e) {
System.err.println("Error: " + e.getMessage());
}
}
}
SecureRandom for cryptographic operations. Do not use java.util.Random as it is not cryptographically strong and can lead to predictable keys, compromising your security.Key Storage and Management
Generating a key is only the first step. Proper key management is paramount for maintaining the security of your encrypted data. Keys should never be hardcoded or stored in plain text. For production environments, consider using Java KeyStore (JKS) or a Hardware Security Module (HSM) to securely store and manage your keys. When a key is no longer needed, it should be securely destroyed.
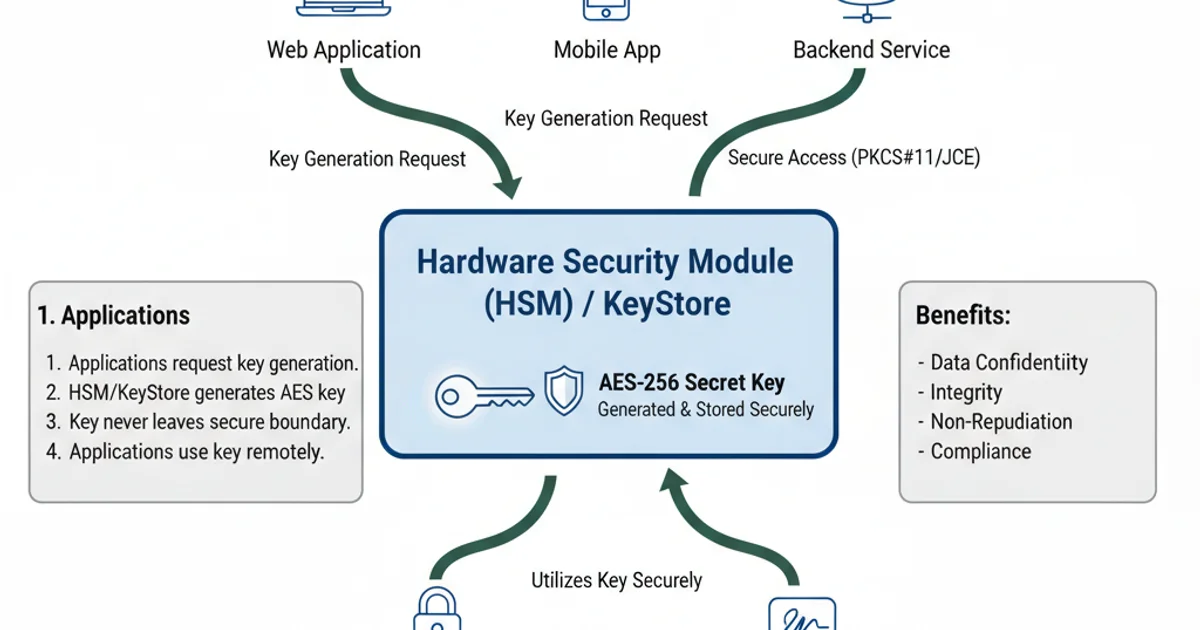
Secure Key Storage Architecture
getEncoded() method on SecretKey returns the raw key bytes. Be extremely careful with these bytes; they represent the secret key itself. Never log them or expose them in insecure ways. If you need to persist the key, encrypt it first or use a secure KeyStore.Exporting and Importing Keys (Advanced)
While direct key generation is preferred, there might be scenarios where you need to export a key (e.g., for transfer to another system) or import a key from raw bytes. This requires careful handling to maintain security. The SecretKeySpec class can be used to reconstruct a SecretKey from its raw byte array.
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
import java.security.NoSuchAlgorithmException;
import java.util.Base64;
public class KeyExportImport {
public static SecretKey generateAesKey(int keySizeBits) throws NoSuchAlgorithmException {
// ... (same as previous example)
return new AesKeyGenerator().generateAesKey(keySizeBits);
}
public static String exportKeyToString(SecretKey key) {
return Base64.getEncoder().encodeToString(key.getEncoded());
}
public static SecretKey importKeyFromString(String encodedKey, String algorithm) {
byte[] decodedKey = Base64.getDecoder().decode(encodedKey);
return new SecretKeySpec(decodedKey, 0, decodedKey.length, algorithm);
}
public static void main(String[] args) {
try {
SecretKey originalKey = generateAesKey(256);
System.out.println("Original Key (bytes length): " + originalKey.getEncoded().length);
String exportedKey = exportKeyToString(originalKey);
System.out.println("Exported Key (Base64): " + exportedKey);
SecretKey importedKey = importKeyFromString(exportedKey, "AES");
System.out.println("Imported Key (bytes length): " + importedKey.getEncoded().length);
// Verify if keys are identical (for demonstration, not for production comparison)
boolean keysMatch = java.util.Arrays.equals(originalKey.getEncoded(), importedKey.getEncoded());
System.out.println("Original and Imported Keys Match: " + keysMatch);
} catch (NoSuchAlgorithmException e) {
System.err.println("Algorithm error: " + e.getMessage());
}
}
}