XMPP + OTR Encryption in PHP
Categories:
Securing XMPP Communication with OTR Encryption in PHP

Explore how to implement Off-the-Record (OTR) encryption for XMPP messaging in PHP, ensuring private and authenticated real-time communication.
In an era where digital privacy is paramount, securing real-time communication protocols like XMPP (Extensible Messaging and Presence Protocol) is crucial. While XMPP offers a robust framework for instant messaging, its core specification doesn't mandate end-to-end encryption. This is where Off-the-Record (OTR) messaging comes into play, providing strong encryption, authentication, deniability, and perfect forward secrecy for XMPP conversations. This article delves into the concepts of OTR and guides you through integrating it with PHP for secure XMPP communication.
Understanding XMPP and OTR
XMPP is an open, XML-based protocol for instant messaging and presence. It's decentralized, extensible, and widely used in various applications. However, without additional security layers, XMPP messages can be intercepted and read. OTR is a cryptographic protocol that addresses these vulnerabilities by adding several key security features:
- Encryption: All messages are encrypted end-to-end, meaning only the sender and intended recipient can read them.
- Authentication: Both parties can verify each other's identity, preventing impersonation.
- Deniability: Messages cannot be cryptographically linked back to the sender after the conversation, providing plausible deniability.
- Perfect Forward Secrecy: If a long-term key is compromised, past session keys remain secure, preventing decryption of previous conversations.
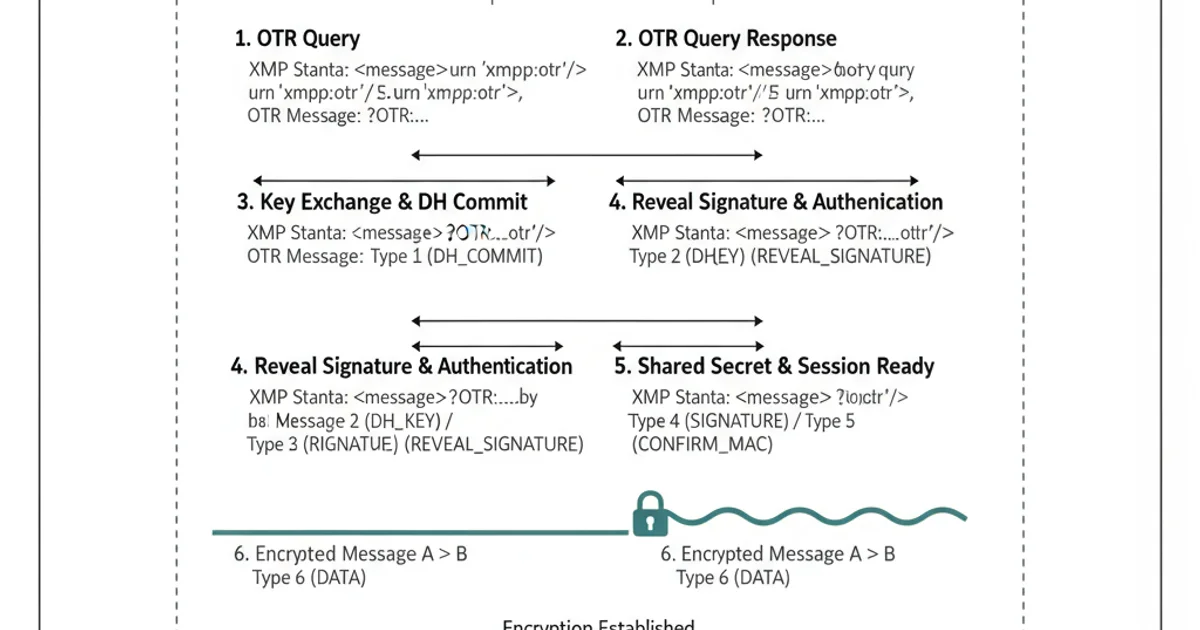
OTR Handshake Process over XMPP
Challenges of OTR Implementation in PHP
Implementing OTR in PHP for XMPP presents several challenges. OTR is a complex cryptographic protocol that requires careful handling of cryptographic primitives, state management, and message parsing. While there are mature OTR libraries available in languages like C (libotr) and Python, a direct, fully-featured OTR library for PHP is not commonly available or maintained for direct XMPP integration.
Therefore, a common approach for PHP applications is to leverage existing OTR implementations through external processes or services. This could involve:
- Using a dedicated OTR proxy/gateway: A separate service (written in Python, Node.js, or C) handles the OTR encryption/decryption and relays messages to/from the PHP application.
- Executing external OTR tools: PHP can execute command-line OTR tools (like
otrtoolif available and suitable) to process messages. - Interfacing with a custom OTR daemon: Building a daemon in a language with strong OTR library support and communicating with it via a local API (e.g., REST, WebSocket).
For the purpose of this article, we'll focus on the conceptual integration and demonstrate how PHP would interact with an assumed OTR processing layer, as building a full OTR library from scratch in PHP is beyond the scope and generally not recommended due to cryptographic complexity.
Conceptual PHP Integration with an OTR Processing Layer
Let's imagine we have an external OTR processing service (e.g., a Python script using python-otr or a Node.js service) that exposes a simple API to encrypt and decrypt messages. Your PHP application would then communicate with this service. This approach decouples the complex cryptographic logic from your PHP application, allowing PHP to focus on XMPP stanza handling and application logic.
Consider a scenario where your PHP application receives an XMPP message. If it's an OTR message, it needs to be passed to the OTR processing layer for decryption. Similarly, when sending a message, it first goes to the OTR layer for encryption before being sent via XMPP.
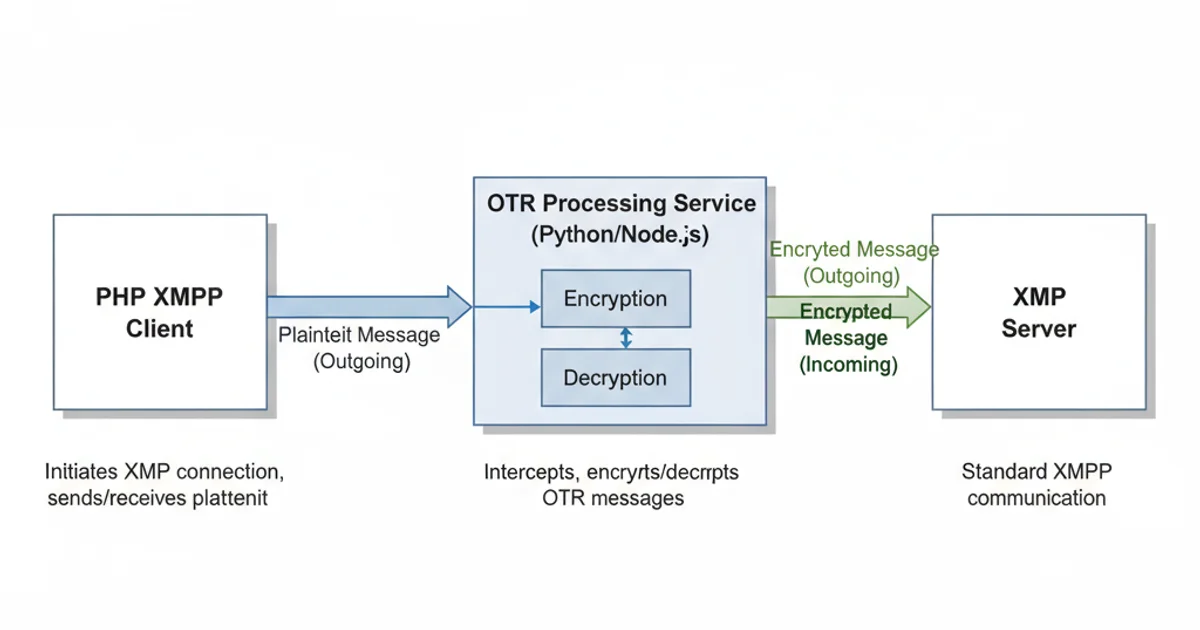
Conceptual Architecture: PHP XMPP Client with External OTR Service
Here's how the interaction might look in PHP, assuming a simple HTTP API for the OTR service:
<?php
class OTRClient
{
private string $otrServiceUrl;
private string $localJid;
private string $remoteJid;
public function __construct(string $otrServiceUrl, string $localJid, string $remoteJid)
{
$this->otrServiceUrl = rtrim($otrServiceUrl, '/');
$this->localJid = $localJid;
$this->remoteJid = $remoteJid;
}
public function encryptMessage(string $plaintext):
{
$payload = [
'action' => 'encrypt',
'local_jid' => $this->localJid,
'remote_jid' => $this->remoteJid,
'message' => $plaintext
];
return $this->sendRequest($payload);
}
public function decryptMessage(string $encryptedMessage):
{
$payload = [
'action' => 'decrypt',
'local_jid' => $this->localJid,
'remote_jid' => $this->remoteJid,
'message' => $encryptedMessage
];
return $this->sendRequest($payload);
}
public function initiateOtrSession():
{
$payload = [
'action' => 'initiate_session',
'local_jid' => $this->localJid,
'remote_jid' => $this->remoteJid
];
return $this->sendRequest($payload);
}
private function sendRequest(array $payload):
{
$ch = curl_init($this->otrServiceUrl . '/process');
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS, json_encode($payload));
curl_setopt($ch, CURLOPT_HTTPHEADER, ['Content-Type: application/json']);
$response = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
curl_close($ch);
if ($httpCode !== 200) {
throw new Exception("OTR Service error: " . $response);
}
$result = json_decode($response, true);
if (json_last_error() !== JSON_ERROR_NONE) {
throw new Exception("Invalid JSON response from OTR Service.");
}
return $result;
}
}
// Example Usage within an XMPP client context
// Assume you have an XMPP client library handling connection and stanza parsing
// Configuration
$otrServiceUrl = 'http://localhost:5000'; // URL of your OTR processing service
$myJid = 'user1@example.com';
$buddyJid = 'user2@example.com';
$otrClient = new OTRClient($otrServiceUrl, $myJid, $buddyJid);
// --- Sending an OTR message ---
try {
$plaintextToSend = "Hello, this is a secret message!";
$encryptionResult = $otrClient->encryptMessage($plaintextToSend);
if (isset($encryptionResult['encrypted_message'])) {
$encryptedXmppBody = $encryptionResult['encrypted_message'];
// Now, send $encryptedXmppBody via your XMPP client library
echo "Sending encrypted message: " . $encryptedXmppBody . "\n";
// Example: $xmppClient->sendMessage($buddyJid, $encryptedXmppBody);
} elseif (isset($encryptionResult['otr_query'])) {
$otrQuery = $encryptionResult['otr_query'];
// Send OTR query to initiate session
echo "Sending OTR query: " . $otrQuery . "\n";
// Example: $xmppClient->sendMessage($buddyJid, $otrQuery);
} else {
echo "OTR service did not return an encrypted message or query.\n";
}
} catch (Exception $e) {
echo "Error encrypting message: " . $e->getMessage() . "\n";
}
// --- Receiving and decrypting an OTR message ---
// Assume $receivedXmppBody is the content of an XMPP message stanza
$receivedXmppBody = '?OTR:AAED...'; // Example OTR message
try {
$decryptionResult = $otrClient->decryptMessage($receivedXmppBody);
if (isset($decryptionResult['plaintext_message'])) {
$decryptedMessage = $decryptionResult['plaintext_message'];
echo "Received decrypted message: " . $decryptedMessage . "\n";
} elseif (isset($decryptionResult['otr_event'])) {
// Handle OTR events like 'session_started', 'authentication_required', etc.
echo "Received OTR event: " . $decryptionResult['otr_event'] . "\n";
} else {
echo "OTR service did not return a plaintext message or event.\n";
}
} catch (Exception $e) {
echo "Error decrypting message: " . $e->getMessage() . "\n";
}
// --- Initiating an OTR session ---
try {
$initiationResult = $otrClient->initiateOtrSession();
if (isset($initiationResult['otr_query'])) {
$otrQuery = $initiationResult['otr_query'];
echo "Initiating OTR session with query: " . $otrQuery . "\n";
// Send this query via XMPP
}
} catch (Exception $e) {
echo "Error initiating OTR session: " . $e->getMessage() . "\n";
}
?>
localhost or via HTTPS with authentication) and handles state management (private keys, session keys) robustly.Setting up a Basic OTR Processing Service (Python Example)
To make the PHP example functional, you'd need an OTR processing service. Here's a very basic Python Flask example using python-otr that could serve as the http://localhost:5000 endpoint from the PHP code. This example is simplified and lacks robust error handling, key management, and multi-user support, but demonstrates the core idea.
import json
from flask import Flask, request, jsonify
from otr import OTR
app = Flask(__name__)
# In a real application, this would be persistent and per-user
# For simplicity, we'll use a global OTR instance for a single conversation
# This is NOT suitable for production multi-user environments.
otr_instances = {}
def get_otr_instance(local_jid, remote_jid):
key = f"{local_jid}-{remote_jid}"
if key not in otr_instances:
# Generate a new private key for each session for demonstration
# In production, keys should be loaded/saved securely.
otr_instances[key] = OTR(privkey=OTR.generate_privkey())
return otr_instances[key]
@app.route('/process', methods=['POST'])
def process_otr():
data = request.json
action = data.get('action')
local_jid = data.get('local_jid')
remote_jid = data.get('remote_jid')
message = data.get('message')
if not all([action, local_jid, remote_jid]):
return jsonify({'error': 'Missing required parameters'}), 400
otr_instance = get_otr_instance(local_jid, remote_jid)
try:
if action == 'encrypt':
# OTR.send() handles both initiating OTR and sending encrypted messages
# It returns (encrypted_message, new_state)
encrypted_message, _ = otr_instance.send(message, remote_jid)
if encrypted_message.startswith('?OTR:'):
return jsonify({'encrypted_message': encrypted_message})
else:
# If it's not an OTR message, it might be an OTR query to initiate
return jsonify({'otr_query': encrypted_message})
elif action == 'decrypt':
# OTR.receive() handles incoming OTR messages and queries
# It returns (plaintext_message, new_state, event)
plaintext, _, event = otr_instance.receive(message, remote_jid)
if plaintext:
return jsonify({'plaintext_message': plaintext})
elif event:
return jsonify({'otr_event': event.name.lower()})
else:
return jsonify({'error': 'Could not decrypt or process OTR message.'}), 400
elif action == 'initiate_session':
# Manually initiate an OTR session by sending an empty message
# This will generate the initial OTR query
otr_query, _ = otr_instance.send('', remote_jid)
return jsonify({'otr_query': otr_query})
else:
return jsonify({'error': 'Invalid action'}), 400
except Exception as e:
return jsonify({'error': str(e)}), 500
if __name__ == '__main__':
app.run(debug=True, port=5000)
1. Install Python OTR Library
First, install the python-otr library and Flask for the OTR processing service: pip install python-otr Flask.
2. Run the Python Service
Save the Python code above as otr_service.py and run it: python otr_service.py. This will start the service on http://localhost:5000.
3. Integrate PHP Client
In your PHP XMPP application, use the OTRClient class to send messages to and receive messages from this Python service. Ensure your XMPP client library is configured to send and receive raw message bodies.
4. Handle OTR States
The python-otr library manages OTR states internally. In a production system, you would need to persist these states (e.g., in a database) for each local_jid-remote_jid pair so that sessions can be resumed across application restarts.