Ping sweep syntax via CMD.exe
Categories:
Mastering Ping Sweeps with CMD.exe for Network Discovery
Learn how to perform basic and advanced ping sweeps using the Windows Command Prompt (CMD.exe) to discover active hosts on a network. This guide covers essential commands, syntax, and practical examples for network reconnaissance.
Ping sweeps are a fundamental technique in network administration and security for identifying active devices within a specified IP range. By sending ICMP (Internet Control Message Protocol) echo requests to multiple hosts and listening for replies, you can quickly determine which IP addresses are currently in use. This article will guide you through performing ping sweeps using the native ping command in CMD.exe, covering various scenarios and providing practical examples.
Understanding the 'ping' Command Basics
The ping command is a simple yet powerful utility available in Windows that sends ICMP echo request packets to a target host and waits for an ICMP echo reply. It's primarily used to test network connectivity and measure round-trip time. When performing a ping sweep, we leverage this command to iterate through a range of IP addresses.
ping 192.168.1.1
Basic ping command to test connectivity to a single host.
Performing a Basic Ping Sweep
CMD.exe does not have a built-in command for sweeping an entire range of IPs directly. However, you can achieve this using a FOR loop, which allows you to iterate through a sequence of numbers (representing the last octet of an IP address) and execute the ping command for each. This method is effective for small to medium-sized subnets.
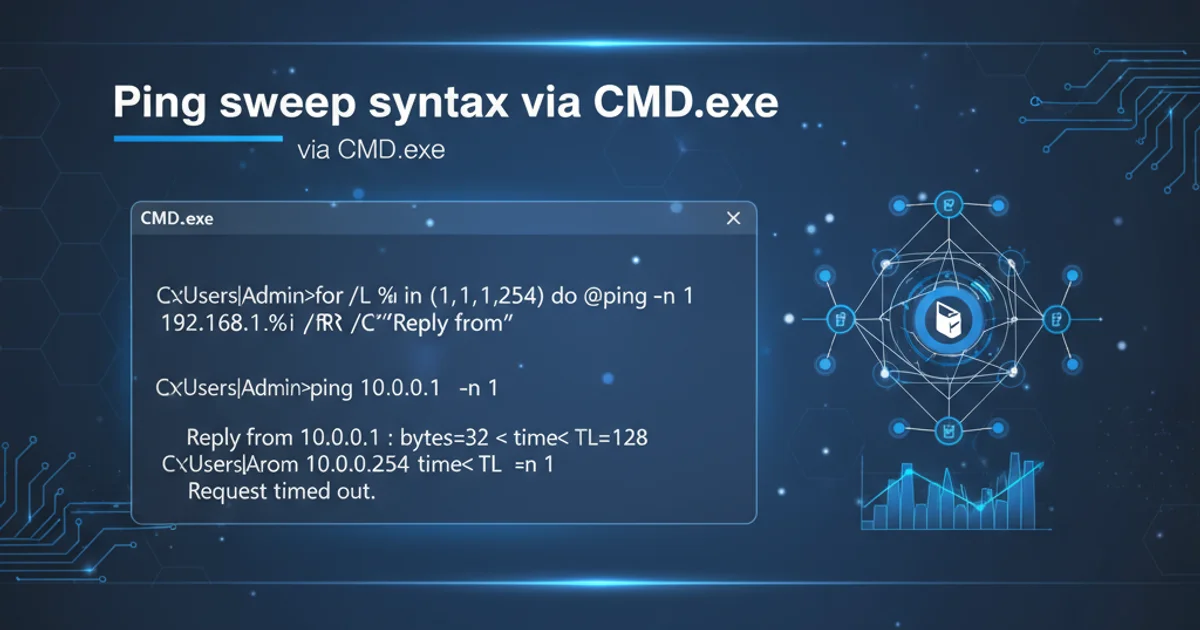
FOR /L %i IN (1,1,254) DO @ping -n 1 192.168.1.%i | findstr "Reply from"
Ping sweep for a /24 subnet (192.168.1.1 to 192.168.1.254).
Let's break down the components of this command:
FOR /L %i IN (1,1,254): This loop iterates a variable%ifrom 1 to 254, incrementing by 1 each time. This covers the typical range for the last octet of an IPv4 address in a /24 subnet.DO: Specifies the command to execute for each iteration.@ping -n 1 192.168.1.%i: Executes thepingcommand.-n 1sends only one echo request, making the sweep faster.192.168.1.%iconstructs the target IP address using the current value of%i.| findstr "Reply from": This pipes the output of thepingcommand tofindstr.findstr "Reply from"filters the output, showing only lines that contain "Reply from", which indicates a successful ping response. This helps in quickly identifying active hosts by suppressing the "Request timed out" messages.
Advanced Ping Sweep Techniques
While the basic FOR loop is functional, you can refine your ping sweeps for better performance or specific needs. For instance, you might want to save the results to a file or sweep a different IP range.
FOR /L %i IN (100,1,150) DO @ping -n 1 192.168.1.%i | findstr "Reply from" >> active_hosts.txt
Ping sweep for a specific range (192.168.1.100-150) and saving results to a file.
In this example, (100,1,150) specifies a loop from 100 to 150. The >> active_hosts.txt redirects the output of findstr (i.e., the successful replies) and appends them to a file named active_hosts.txt. If the file doesn't exist, it will be created.
flowchart TD
A[Start Ping Sweep] --> B{"Define IP Range (e.g., 192.168.1.1-254)"}
B --> C{Loop through each IP in range}
C --> D["Construct Ping Command (e.g., ping -n 1 192.168.1.X)"]
D --> E["Execute Ping Command"]
E --> F{"Filter Output for 'Reply from'"}
F -- "Reply Found" --> G["Identify Active Host"]
F -- "No Reply" --> H["Host Inactive/Unreachable"]
G --> C
H --> C
C -- "End of Range" --> I[End Ping Sweep]Workflow of a CMD.exe based ping sweep.
Considerations for Different Subnet Masks
The FOR /L loop is ideal for iterating through the last octet of a /24 subnet. For other subnet masks, you might need to adjust the loop or use nested loops. For example, a /16 subnet (e.g., 192.168.0.0/16) would require iterating through two octets.
FOR /L %i IN (0,1,255) DO FOR /L %j IN (1,1,254) DO @ping -n 1 192.168.%i.%j | findstr "Reply from"
Nested FOR loop for a /16 subnet (192.168.0.1 to 192.168.255.254).
This nested loop structure allows you to cover a much larger IP range, but it will take significantly longer to complete. The outer loop iterates through the third octet (%i), and the inner loop iterates through the fourth octet (%j). Remember to adjust the starting and ending values of the loops to match your specific subnet requirements.
%%i and %%j instead of %i and %j for the loop variables. The single percent sign is for direct command-line execution, while double percent signs are for batch scripts.