Connect-VIServer not working with passed credentials, but works with integrated authentication
Categories:
Troubleshooting Connect-VIServer with Explicit Credentials in PowerCLI
Learn why Connect-VIServer might fail with passed credentials but succeed with integrated authentication, and discover solutions for robust PowerCLI scripting.
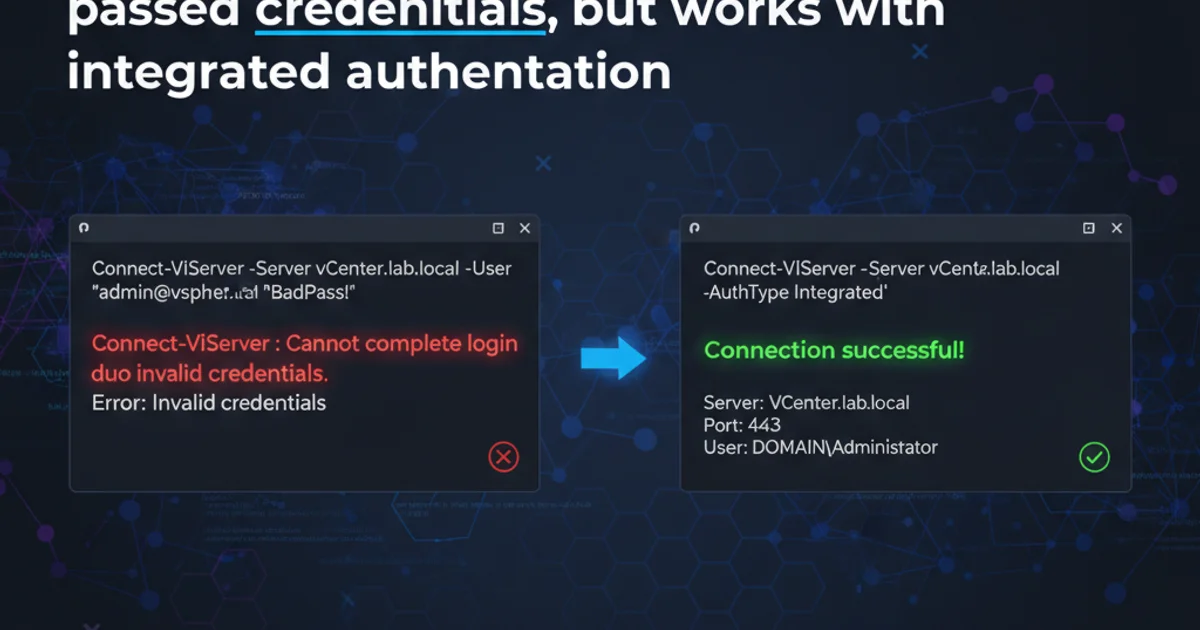
Connecting to VMware vCenter Server using PowerCLI's Connect-VIServer cmdlet is a fundamental operation for any VMware administrator. While integrated Windows authentication often works seamlessly, you might encounter scenarios where explicitly passing credentials fails, even if the credentials themselves are valid. This article delves into the common reasons behind this discrepancy and provides practical solutions to ensure your PowerCLI scripts connect reliably.
Understanding the Authentication Flow
When you execute Connect-VIServer, PowerCLI attempts to authenticate with the vCenter Server. The method of authentication can significantly impact success. Integrated Windows authentication (often used when running PowerCLI on a domain-joined machine with a user account that has vCenter permissions) leverages Kerberos or NTLM to pass the current user's security context. When you explicitly provide credentials using the -Credential parameter, PowerCLI constructs a PSCredential object and attempts to authenticate using that specific username and password. The failure to connect with explicit credentials, while integrated authentication works, often points to issues with how these credentials are presented, network trust, or vCenter's authentication configuration.
flowchart TD
A[PowerCLI Host] --> B{Connect-VIServer Command}
B --> C{Integrated Auth?}
C -- Yes --> D[Current User's Security Context]
C -- No --> E[Explicit -Credential Parameter]
D --> F{Kerberos/NTLM}
E --> G{Username/Password}
F --> H[vCenter Server]
G --> H
H -- Success --> I[Connected Session]
H -- Failure --> J[Authentication Error]
J --> K[Troubleshooting Steps]Authentication flow for Connect-VIServer
Common Causes and Solutions
Several factors can lead to Connect-VIServer failing with explicit credentials. Identifying the root cause is crucial for applying the correct fix. Here are the most common scenarios and their resolutions:
1. Incorrect Credential Format or Domain
One of the most frequent issues is providing the username in an incorrect format. vCenter Server expects specific formats depending on whether the user is local to vCenter or part of an Active Directory domain.
$username = "DOMAIN\username"
$password = "YourPassword"
$cred = New-Object System.Management.Automation.PSCredential($username, (ConvertTo-SecureString $password -AsPlainText -Force))
Connect-VIServer -Server "vcenter.yourdomain.com" -Credential $cred
Correctly formatting credentials for a domain user
administrator@vsphere.local), the username format should typically be username@domain or simply username if vsphere.local is the default. For Active Directory users, use DOMAIN\username or username@DOMAIN.COM.2. DNS Resolution and Network Connectivity
Even if integrated authentication works, explicit credential failures can sometimes be masked network issues. Ensure your PowerCLI host can resolve the vCenter Server's hostname and communicate on the necessary ports (typically 443 for HTTPS).
Test-NetConnection -ComputerName "vcenter.yourdomain.com" -Port 443
Testing network connectivity to vCenter Server
3. PowerCLI Version Compatibility
Outdated PowerCLI modules can sometimes lead to unexpected authentication issues, especially after vCenter Server upgrades. Ensure you are using a PowerCLI version compatible with your vCenter Server version.
Get-Module -Name VMware.PowerCLI -ListAvailable | Select-Object Version, Path
# To update (run as administrator):
Update-Module -Name VMware.PowerCLI
Checking and updating your PowerCLI module
4. SSL Certificate Issues
While less common for explicit credentials than for integrated, SSL certificate warnings or errors can prevent a connection. If you're using self-signed certificates, you might need to temporarily disable certificate validation for testing, though this is not recommended for production.
Set-PowerCLIConfiguration -InvalidCertificateAction Ignore -Scope Session
Connect-VIServer -Server "vcenter.yourdomain.com" -Credential $cred
Set-PowerCLIConfiguration -InvalidCertificateAction Warn -Scope Session # Revert after testing
Temporarily ignoring invalid SSL certificates (use with caution)
-InvalidCertificateAction Ignore) should only be used for testing in non-production environments. In production, ensure your vCenter Server has valid, trusted SSL certificates to maintain security.5. Service Account Permissions and Lockouts
If you're using a service account, verify that it has the necessary permissions within vCenter Server. Also, check Active Directory for account lockouts, especially if the script runs frequently or has had incorrect credentials supplied in the past.
1. Verify vCenter Permissions
Log into the vSphere Client with an administrative account. Navigate to 'Administration' > 'Roles' or 'Global Permissions' and ensure the service account has at least 'Read-only' access at the vCenter level, or more specific permissions as required by your script.
2. Check Active Directory Account Status
On a domain controller or a machine with RSAT tools, open 'Active Directory Users and Computers'. Locate the service account and check its properties for any lockout status or password expiration settings.
6. PowerShell Execution Policy
While not directly related to credential passing, an overly restrictive PowerShell execution policy can prevent scripts from running, leading to perceived connection issues. Ensure your policy allows script execution.
Get-ExecutionPolicy
# To set a less restrictive policy (e.g., RemoteSigned):
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUser
Checking and setting PowerShell execution policy
RemoteSigned execution policy is a good balance for most environments, allowing local scripts to run without signing, but requiring scripts downloaded from the internet to be signed by a trusted publisher.