How to check if a program is using .NET?
Categories:
How to Determine if a Program is Using .NET

Learn various methods to identify if an executable or running process is built on the .NET framework, from simple file inspection to advanced tooling.
Identifying whether a program utilizes the .NET framework can be crucial for troubleshooting, compatibility checks, security analysis, or development planning. While some applications explicitly state their dependencies, many do not. This article will guide you through several techniques, ranging from quick visual checks to using specialized tools, to confidently determine if a program is a .NET application.
Method 1: File System Inspection
The simplest way to get an initial hint about a program's .NET dependency is by examining its installation directory or the executable itself. .NET applications often come with specific files or exhibit characteristics that are easy to spot.
flowchart TD
A[Start: Inspect Program Files] --> B{Look for .config files?}
B -->|Yes| C[Presence of AppName.exe.config suggests .NET]
B -->|No| D{Look for .dll files with 'System.' prefix?}
D -->|Yes| E[Many System.*.dll files strongly suggest .NET]
D -->|No| F{Check executable with a text editor?}
F -->|Yes| G[Search for 'Microsoft.NETFramework' or 'CorExitProcess']
F -->|No| H[Consider other methods]
C --> I[Likely .NET]
E --> I
G --> I
I --> J[End]Flowchart for file system inspection to identify .NET applications.
Key Indicators:
- Configuration Files (.config): .NET applications frequently use configuration files named
[ApplicationName].exe.config(e.g.,MyApp.exe.config). The presence of such a file, especially with XML content, is a strong indicator. - DLL Dependencies: Look for DLLs (Dynamic Link Libraries) in the application's directory that start with
System.(e.g.,System.Windows.Forms.dll,System.Data.dll). While not exclusive to .NET, a large number of these files is highly suggestive. - Executable Content: Opening the executable (
.exe) in a plain text editor (like Notepad++) and searching for strings likeMicrosoft.NETFramework,CorExitProcess, ormscoree.dllcan reveal its .NET nature. These strings are often embedded within the executable's metadata.
<?xml version="1.0" encoding="utf-8" ?>
<configuration>
<startup>
<supportedRuntime version="v4.0" sku=".NETFramework,Version=v4.7.2" />
</startup>
</configuration>
Example of a .NET application configuration file (.exe.config).
System.*.dll files if they interact with .NET components via COM interop. However, a significant number usually points to a full .NET dependency.Method 2: Using Process Explorer or Task Manager
For running applications, process monitoring tools can provide insights into the loaded modules and environment variables, which can help identify .NET processes.
Using Process Explorer (Sysinternals):
Process Explorer is a powerful tool that offers more detail than the standard Task Manager. To check for .NET:
- Download and Run: Get Process Explorer from Microsoft Sysinternals.
- Find the Process: Locate the target application's process in the list.
- Check DLLs: Double-click the process or go to
View > Lower Pane View > DLLs. Look formscoree.dll,clr.dll, orcoreclr.dllin the loaded modules. The presence of these indicates a .NET runtime is loaded. - Check .NET Assemblies: Process Explorer can also show loaded .NET assemblies directly. Go to
View > Lower Pane View > .NET Assemblies(if available and applicable to the process).
Using Task Manager (Windows 10/11):
While less detailed, Task Manager can offer a quick hint:
- Open Task Manager: Press
Ctrl+Shift+Esc. - Go to Details Tab: Find the process.
- Add 'Command Line' Column: Right-click on the column headers and select 'Command line'. Sometimes, the command line might reveal paths to
dotnet.exeor other .NET-related arguments.
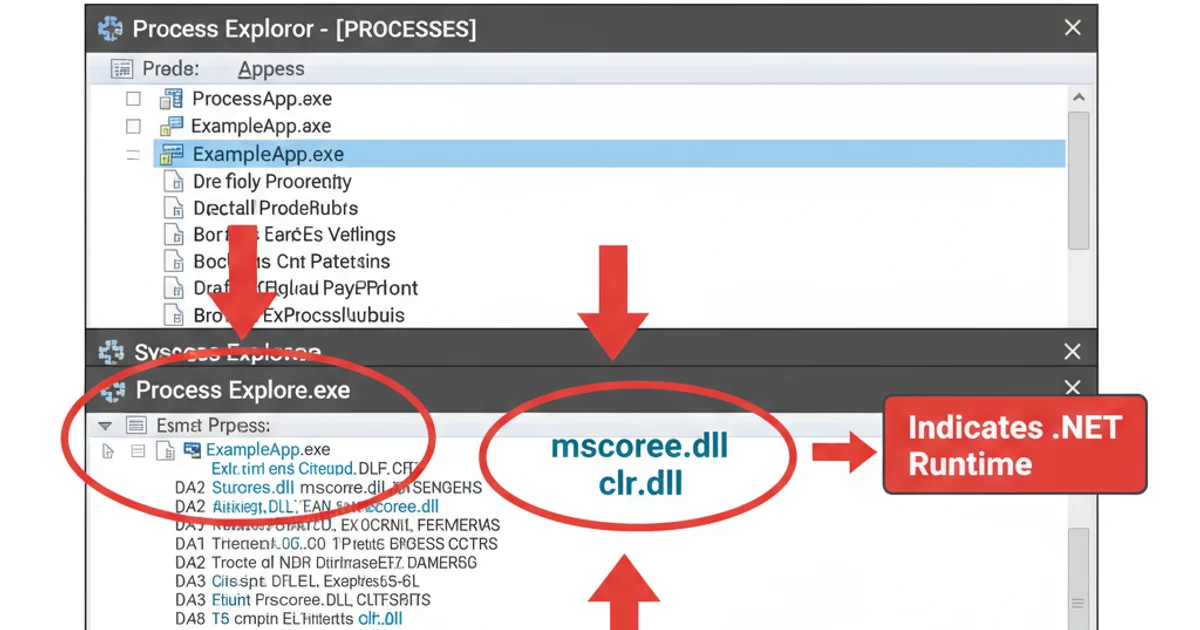
Process Explorer displaying loaded .NET runtime DLLs.
Method 3: Utilizing .NET-Specific Tools
Several specialized tools are designed to inspect executables and provide definitive answers regarding their .NET nature and even the specific framework version.
1. ILSpy or dnSpy:
These are .NET decompilers. If you can open an executable in ILSpy or dnSpy and it successfully decompiles into C# or VB.NET code, then it is unequivocally a .NET assembly. These tools will also tell you the target .NET Framework or .NET Core version.
2. CorFlags.exe:
CorFlags.exe is a command-line tool that comes with the .NET Framework SDK. It can inspect a PE (Portable Executable) file and report whether it's a .NET assembly and its associated flags.
To use it, open a Developer Command Prompt for Visual Studio or a regular command prompt with the .NET SDK installed, and run:
CorFlags.exe "C:\Path\To\Your\Application.exe"
Using CorFlags.exe to inspect an executable.
Look for output indicating CLR Header: 1 and a 32BITREQ or 32BITPREFERRED flag. The presence of a CLR Header confirms it's a managed assembly.
3. Detect-Managed-Code.ps1 (PowerShell Script):
This is a community-contributed PowerShell script that can scan a directory for managed executables. It's particularly useful for batch checking.
# Example usage (script not included, but widely available online)
Get-ChildItem -Path "C:\Program Files\YourApp" -Filter "*.exe" | ForEach-Object {
if (Test-Path $_.FullName) {
try {
$file = [System.Reflection.Assembly]::LoadFile($_.FullName)
Write-Host "$($_.Name) is a .NET assembly (Version: $($file.ImageRuntimeVersion))"
} catch {
Write-Host "$($_.Name) is not a .NET assembly or cannot be loaded."
}
}
}
This script attempts to load the executable as a .NET assembly. If successful, it's a .NET program.
1. Inspect File System for Clues
Navigate to the program's installation directory and look for .config files or numerous System.*.dll files. Open the executable in a text editor and search for .NET related strings.
2. Monitor Running Processes
Use Process Explorer to examine the loaded DLLs of a running application. Look for mscoree.dll, clr.dll, or coreclr.dll which signify a .NET runtime.
3. Utilize .NET Specific Tools
For definitive confirmation, try opening the executable with a .NET decompiler like ILSpy or use the CorFlags.exe command-line tool to check for a CLR Header.