Hidden/Open words in an Image file such as PNG or JGP
Categories:
Steganography: Hiding and Extracting Text in Image Files

Explore the fascinating world of steganography, focusing on techniques to embed and retrieve hidden text within common image formats like PNG and JPEG.
Steganography, derived from the Greek words 'steganos' (covered) and 'graphein' (to write), is the art and science of concealing a message within another message or a physical object. Unlike cryptography, which scrambles a message to make it unreadable without a key, steganography aims to hide the very existence of the message. In the digital realm, image files are popular carriers for hidden information due to their often large size and the human eye's limited ability to detect subtle changes.
Understanding Image File Structures
Before diving into hiding text, it's crucial to understand how image files store data. Both PNG and JPEG formats handle image data differently, which impacts the steganographic techniques that can be applied.
PNG (Portable Network Graphics) is a lossless compression format, meaning it retains all original image data. This makes it suitable for techniques that modify pixel data directly, as these changes are preserved. PNG files store pixel data as a grid of RGB (Red, Green, Blue) or RGBA (Red, Green, Blue, Alpha) values, where each color component is typically represented by 8 bits.
JPEG (Joint Photographic Experts Group) is a lossy compression format, designed to reduce file size by discarding some image information that is less perceptible to the human eye. This lossy nature makes steganography more challenging, as hidden data might be lost during compression or re-saving. JPEG uses Discrete Cosine Transform (DCT) to convert image data into frequency components, which are then quantized and encoded.
flowchart TD
A[Image File] --> B{Choose Format}
B -->|PNG| C[Lossless Compression]
B -->|JPEG| D[Lossy Compression]
C --> E[Direct Pixel Manipulation]
D --> F[DCT Coefficient Modification]
E --> G[High Data Fidelity]
F --> H[Risk of Data Loss]
G --> I[Steganography Method]
H --> IDecision flow for steganography based on image format characteristics.
Least Significant Bit (LSB) Steganography
One of the simplest and most common methods for hiding data in images is Least Significant Bit (LSB) steganography. This technique modifies the least significant bit of each color component (Red, Green, Blue) in a pixel. Since the LSB contributes the least to the overall color value, changing it typically results in a color difference that is imperceptible to the human eye.
For example, if a pixel's red component is 11010010 (decimal 210), changing its LSB to 0 would make it 11010010 (still 210) or to 1 would make it 11010011 (decimal 211). This minor change is visually negligible. By iterating through the pixels of an image and embedding bits of the secret message into the LSBs of their color channels, a significant amount of data can be hidden. PNG files are ideal for LSB steganography due to their lossless nature.
from PIL import Image
def hide_text_lsb(image_path, text_to_hide, output_path):
img = Image.open(image_path)
width, height = img.size
binary_text = ''.join(format(ord(char), '08b') for char in text_to_hide)
binary_text += '1111111111111110' # Delimiter
if len(binary_text) > width * height * 3: # 3 color channels per pixel
raise ValueError("Text too long to hide in this image.")
data_index = 0
for y in range(height):
for x in range(width):
pixel = list(img.getpixel((x, y)))
for n in range(3): # R, G, B channels
if data_index < len(binary_text):
pixel[n] = pixel[n] & ~1 | int(binary_text[data_index])
data_index += 1
img.putpixel((x, y), tuple(pixel))
img.save(output_path)
def extract_text_lsb(image_path):
img = Image.open(image_path)
width, height = img.size
binary_data = ""
for y in range(height):
for x in range(width):
pixel = img.getpixel((x, y))
for n in range(3): # R, G, B channels
binary_data += str(pixel[n] & 1)
# Check for delimiter
if binary_data[-16:] == '1111111111111110':
try:
all_bytes = [binary_data[i:i+8] for i in range(0, len(binary_data)-16, 8)]
decoded_text = "".join(chr(int(byte, 2)) for byte in all_bytes)
return decoded_text
except ValueError:
return "Error decoding text."
return "No hidden text found or delimiter not reached."
# Example Usage:
# hide_text_lsb('input.png', 'This is a secret message!', 'output_hidden.png')
# extracted_message = extract_text_lsb('output_hidden.png')
# print(f"Extracted: {extracted_message}")
Python code for LSB steganography to hide and extract text in PNG images using the Pillow library.
Challenges and Detection
While LSB steganography is simple, it's also relatively easy to detect. Statistical analysis of pixel values can reveal anomalies introduced by hidden data. For instance, a sudden increase in the number of pixels with even or odd LSBs can indicate the presence of a hidden message. More sophisticated steganographic methods exist, such as those that modify Discrete Cosine Transform (DCT) coefficients in JPEG images, or adaptive steganography that embeds data in 'noisy' areas of an image where changes are less noticeable.
Detection tools, known as steganalysis tools, employ various algorithms to identify steganographic content. These tools often look for statistical deviations, patterns, or changes in image properties that are characteristic of data embedding. The ongoing battle between steganography and steganalysis drives continuous innovation in both fields.
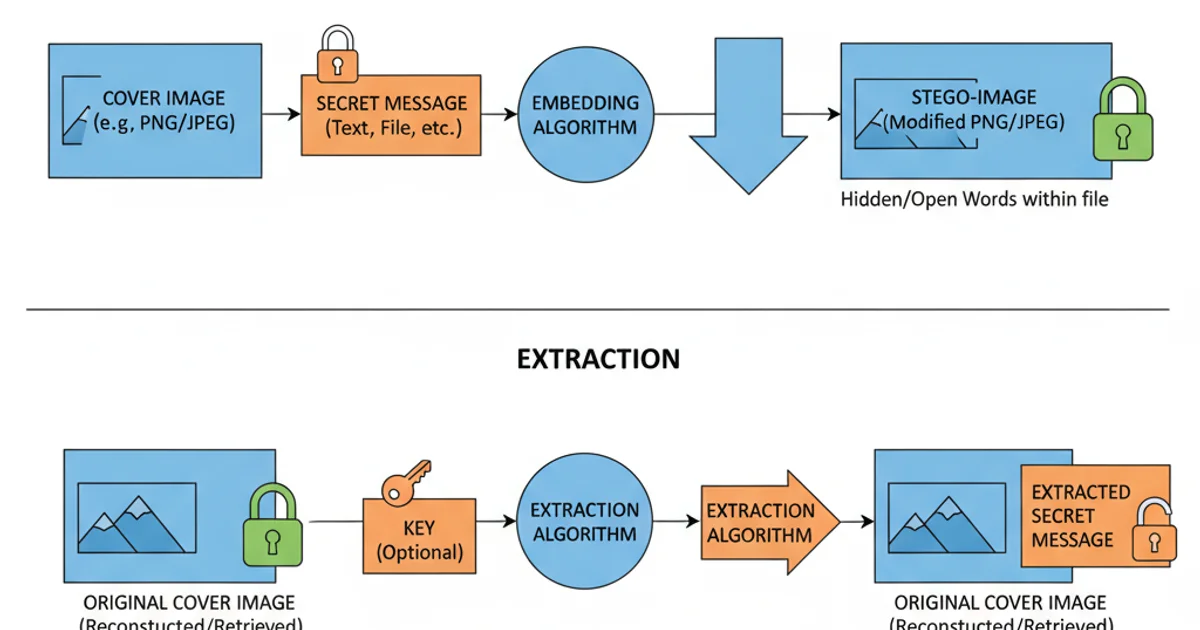
The basic process of steganography: embedding and extraction.
1. Prepare Your Image and Message
Choose a suitable image (preferably PNG for LSB) and the text you wish to hide. Ensure the image is large enough to accommodate the message.
2. Implement Embedding Logic
Write or use a script (like the Python example provided) that modifies the LSBs of the image's pixel data to embed your text. Remember to include a delimiter to mark the end of your message.
3. Save the Stego-Image
Save the modified image. Be cautious with JPEG, as re-saving can introduce lossy compression that might corrupt your hidden data. PNG is generally safer.
4. Implement Extraction Logic
Develop a corresponding script that reads the LSBs from the stego-image, reconstructs the binary data, and converts it back into readable text, stopping at the predefined delimiter.
5. Verify Extraction
Test your extraction process to ensure the original message can be perfectly retrieved from the stego-image.