Differences between "BEGIN RSA PRIVATE KEY" and "BEGIN PRIVATE KEY"
Categories:
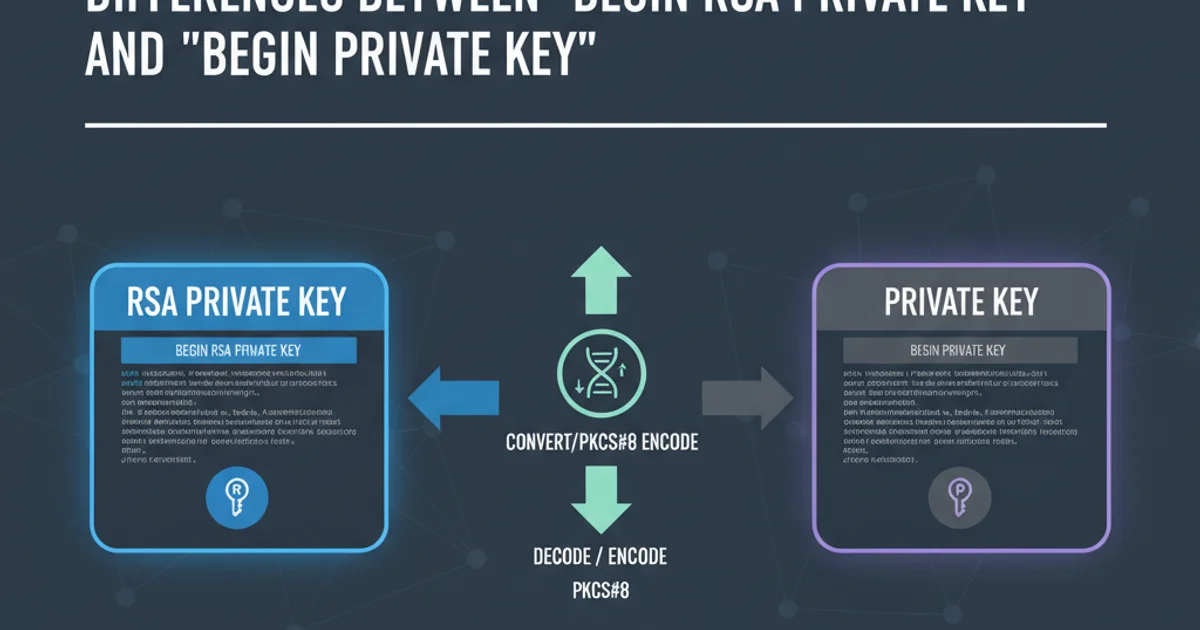
Understanding Private Key Formats: 'BEGIN RSA PRIVATE KEY' vs. 'BEGIN PRIVATE KEY'
Explore the differences between traditional PKCS#1 RSA private keys and the more modern PKCS#8 format, understanding their structure, compatibility, and when to use each.
When working with OpenSSL and cryptographic keys, you'll often encounter private keys encapsulated within PEM-encoded blocks. Two common headers for these blocks are BEGIN RSA PRIVATE KEY and BEGIN PRIVATE KEY. While both denote a private key, they represent different underlying formats, which can lead to compatibility issues if not understood correctly. This article will demystify these formats, explain their origins, and guide you on how to convert between them.
The 'BEGIN RSA PRIVATE KEY' Format (PKCS#1)
The BEGIN RSA PRIVATE KEY header signifies a private key formatted according to PKCS#1 (Public-Key Cryptography Standards #1). This is a legacy format specifically designed for RSA keys. It directly contains the mathematical components of an RSA private key, such as the modulus (n), public exponent (e), private exponent (d), and various prime factors (p, q, dp, dq, qi). Because it's RSA-specific, it cannot encapsulate private keys from other algorithms like ECC (Elliptic Curve Cryptography) or DSA (Digital Signature Algorithm).
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAw+g+9b...
-----END RSA PRIVATE KEY-----
Example of a PKCS#1 formatted RSA private key.
The 'BEGIN PRIVATE KEY' Format (PKCS#8)
The BEGIN PRIVATE KEY header, on the other hand, indicates a private key formatted according to PKCS#8. This is a more modern and universal format. PKCS#8 acts as a container that can hold private keys of any algorithm (RSA, ECC, DSA, etc.). It includes an Object Identifier (OID) that specifies the algorithm of the enclosed key, making it self-describing. This flexibility makes PKCS#8 the preferred format for modern applications and libraries that need to handle various cryptographic algorithms.
-----BEGIN PRIVATE KEY-----
MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEAAoGBAO...
-----END PRIVATE KEY-----
Example of a PKCS#8 formatted private key (could be RSA, ECC, etc.).
flowchart TD
A[Private Key Data] --> B{Algorithm?}
B -->|RSA| C["PKCS#1 (BEGIN RSA PRIVATE KEY)"]
B -->|Any Algorithm| D["PKCS#8 (BEGIN PRIVATE KEY)"]
C --> E[RSA-specific components]
D --> F[Algorithm OID + Encapsulated Key]
style C fill:#f9f,stroke:#333,stroke-width:2px
style D fill:#bbf,stroke:#333,stroke-width:2pxComparison of PKCS#1 and PKCS#8 key formats.
cryptography library) prefer or even require PKCS#8 formatted keys for their flexibility and algorithm agnosticism. If you encounter issues loading a key, converting it to PKCS#8 is often a good first troubleshooting step.Converting Between Formats with OpenSSL
OpenSSL provides robust tools for converting private keys between these formats. This is particularly useful when you have a key in one format but your application or system expects the other.
1. Converting PKCS#1 RSA to PKCS#8
To convert an RSA private key from the PKCS#1 format (BEGIN RSA PRIVATE KEY) to the more general PKCS#8 format (BEGIN PRIVATE KEY), use the following OpenSSL command. This is often necessary when integrating with modern systems.
2. Converting PKCS#8 to PKCS#1 RSA
If you have a PKCS#8 formatted key that specifically contains an RSA private key, and you need to convert it back to the legacy PKCS#1 format (BEGIN RSA PRIVATE KEY), use this command. Be aware that this conversion is only possible if the PKCS#8 key is indeed an RSA key.
PKCS#1 to PKCS#8
openssl rsa -in rsa_pkcs1.pem -outform PEM -out pkcs8_private.pem
PKCS#8 to PKCS#1
openssl pkcs8 -in pkcs8_private.pem -nocrypt -out rsa_pkcs1.pem
-nocrypt flag in the PKCS#8 to PKCS#1 conversion removes any encryption, which might not be desirable for security. For encrypted PKCS#8 keys, you might need to decrypt first or use appropriate flags to re-encrypt.