How to decode a CSR File?
Categories:
Decoding a CSR File: Understanding Your Certificate Signing Request

Learn how to decode and inspect the contents of a Certificate Signing Request (CSR) file, a crucial step in the digital certificate issuance process.
A Certificate Signing Request (CSR) is a block of encoded text that contains information about the entity requesting a digital certificate. When you apply for an SSL/TLS certificate, you generate a CSR on your server. This CSR is then sent to a Certificate Authority (CA) for verification and certificate issuance. Understanding how to decode a CSR is essential for verifying its contents before submission, troubleshooting issues, or simply inspecting an existing request.
What is a CSR and Why Decode It?
A CSR typically contains your public key and distinguished name information, such as your organization's name, common name (domain name), locality, state, and country. It's encoded in a standard format, usually PKCS#10, and often presented in PEM (Privacy-Enhanced Mail) format, which is a Base64-encoded ASCII representation. Decoding a CSR allows you to:
- Verify Information: Ensure all details (domain name, organization, etc.) are correct before sending it to a CA.
- Troubleshoot: Identify discrepancies or errors that might cause certificate issuance failures.
- Audit: Confirm the public key and other parameters embedded within the request.
- Understand Structure: Gain insight into the components of a digital certificate request.
flowchart TD
A[Generate Private Key] --> B[Generate CSR (with Public Key & Info)]
B --> C{Decode CSR?}
C -->|Yes| D[Inspect CSR Contents]
D --> E[Submit CSR to CA]
C -->|No| E[Submit CSR to CA]
E --> F[CA Issues Certificate]
F --> G[Install Certificate]Typical Certificate Signing Request (CSR) Workflow
Decoding CSR Files Using OpenSSL
OpenSSL is a powerful, open-source command-line tool widely used for SSL/TLS operations, including generating and decoding CSRs. It's available on most Unix-like systems and can be installed on Windows. The primary command for decoding a CSR is openssl req -in your_csr.csr -noout -text.
openssl req -in your_csr.csr -noout -text
Basic OpenSSL command to decode a CSR file.
Let's break down the command:
openssl req: This specifies that we are working with a Certificate Signing Request.-in your_csr.csr: This flag indicates the input file, which is your CSR file. Replaceyour_csr.csrwith the actual path to your CSR.-noout: This option prevents OpenSSL from outputting the encoded version of the CSR again. We only want the decoded text.-text: This crucial flag tells OpenSSL to output the CSR's contents in a human-readable text format.
pbpaste | openssl req -noout -text on macOS or similar methods on other OSes.Interpreting the Decoded Output
After running the OpenSSL command, you'll see a detailed output. Here's what to look for:
Certificate Request:: The header indicating the start of the CSR details.Data:: Contains the main body of the request.Version:: The version of the PKCS#10 standard used (usually 0).Subject:: This is the Distinguished Name (DN) of the entity requesting the certificate. It includes fields like:C(Country)ST(State or Province)L(Locality or City)O(Organization Name)OU(Organizational Unit Name)CN(Common Name - typically your domain name, e.g.,www.example.com)
Subject Public Key Info:: Details about the public key included in the CSR, including the algorithm (e.g., RSA) and the public key itself.Signature Algorithm:: The algorithm used to sign the CSR (e.g.,sha256WithRSAEncryption).Signature Value:: The actual digital signature of the CSR, generated using the corresponding private key.Attributes:: This section might contain additional attributes, most notablyX509v3 Subject Alternative Name(SANs) if your CSR includes multiple domain names.
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=US, ST=California, L=San Francisco, O=Example Corp, OU=Web Security, CN=www.example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:c1:a2:b3:c4:d5:e6:f7:08:19:2a:3b:4c:5d:6e:7f:
...
Exponent: 65537 (0x10001)
Attributes:
a0:00
Signature Algorithm: sha256WithRSAEncryption
30:45:02:21:00:a1:b2:c3:d4:e5:f6:g7:h8:i9:j0:k1:l2:m3:n4:o5:p6:
...
Example of decoded CSR output from OpenSSL.
Common Name (CN) in the Subject field exactly matches the domain name you intend to secure. For wildcard certificates, it should be in the format *.example.com.Online CSR Decoders
While OpenSSL is the most robust method, several online tools can also decode CSRs. These are convenient for quick checks but should be used with caution, especially for sensitive information. Always ensure you are using a reputable and secure online decoder.
Common online CSR decoders include those provided by:
- SSL Shopper
- DigiCert
- Namecheap
These tools typically involve pasting your CSR text into a form and clicking a 'Decode' or 'Check' button. They provide a similar human-readable output to OpenSSL.
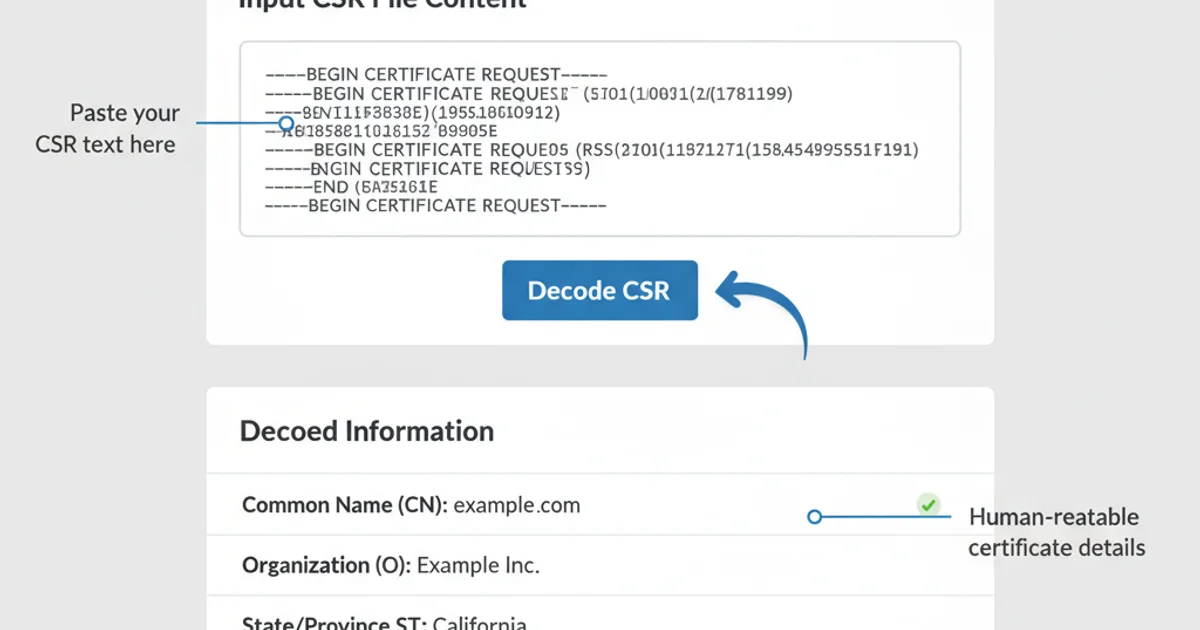
An example of an online CSR decoder interface.
Decoding a CSR is a straightforward process that provides valuable insight into your certificate request. Whether you use OpenSSL or an online tool, understanding the contents of your CSR is a critical step in managing your digital certificates effectively.