Understanding REST: Verbs, error codes, and authentication
Categories:
Understanding REST: Verbs, Error Codes, and Authentication
Dive into the core principles of RESTful APIs, exploring HTTP methods, standard error responses, and common authentication strategies for secure and efficient web service interactions.
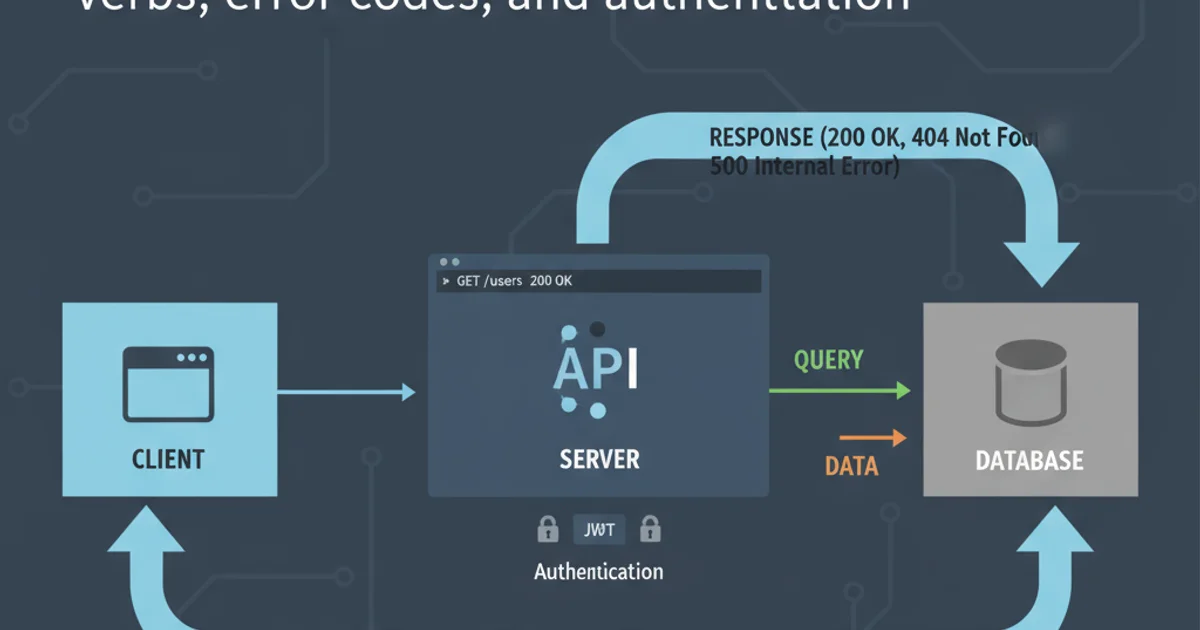
Representational State Transfer (REST) is an architectural style for designing networked applications. It relies on a stateless, client-server communication model, using standard HTTP methods to perform operations on resources. Understanding the fundamental components of REST—HTTP verbs, appropriate error codes, and robust authentication mechanisms—is crucial for building scalable, maintainable, and secure web services.
HTTP Verbs: The Language of REST
HTTP verbs, also known as methods, define the type of action to be performed on a resource identified by a URL. Each verb has a specific semantic meaning, guiding how clients and servers interact. Adhering to these semantics ensures predictability and interoperability in RESTful APIs.
flowchart TD
Client -- Request --> Server
subgraph Client Actions
A[GET /resources] --> B["Retrieve (Read)"]
C[POST /resources] --> D["Create (Add)"]
E[PUT /resources/{id}] --> F["Update (Replace All)"]
G[PATCH /resources/{id}] --> H["Update (Partial)"]
I[DELETE /resources/{id}] --> J["Delete"]
end
B --> Server
D --> Server
F --> Server
H --> Server
J --> Server
Server -- Response --> ClientCommon HTTP Verbs and Their Actions in a RESTful API
Here's a breakdown of the most commonly used HTTP verbs:
PUT, DELETE, and GET. An idempotent operation produces the same result no matter how many times it's executed. POST is generally not idempotent, as repeated requests can create duplicate resources.Standard HTTP Error Codes for REST APIs
When things go wrong, a well-designed REST API communicates the problem clearly using standard HTTP status codes. These codes provide immediate feedback to the client about the nature of the issue, allowing for appropriate error handling. Grouped by their first digit, these codes offer a quick understanding of the response category.
Below are some of the most frequently encountered HTTP status codes in RESTful services:
{
"status": 404,
"error": "Not Found",
"message": "The requested resource could not be found.",
"details": "Please check the URL and try again."
}
Example of a 404 Not Found error response body
Authentication in RESTful Services
Authentication is the process of verifying a client's identity, ensuring that only authorized users or applications can access protected resources. REST APIs, being stateless, require each request to carry authentication information. Several methods exist, each with its own trade-offs regarding security, complexity, and usability.
sequenceDiagram
actor User
participant Client
participant Server
participant AuthProvider
User->>Client: Login (Username/Password)
Client->>Server: POST /login
Server->>AuthProvider: Verify Credentials
AuthProvider-->>Server: Token (e.g., JWT)
Server-->>Client: 200 OK + Token
Client->>Server: GET /protected_resource (with Token in Header)
Server->>Server: Validate Token
Server-->>Client: 200 OK + Resource Data
Client->>Server: GET /another_protected_resource (with Token in Header)
Server->>Server: Validate Token
Server-->>Client: 401 Unauthorized (if token invalid/expired)Sequence Diagram for Token-Based Authentication (e.g., JWT)
Common authentication methods include:
- Basic Authentication: Sends username and password with each request, base64-encoded. Simple but insecure without HTTPS.
- API Keys: A unique key sent in the header or query parameter. Easy to implement but offers limited security and no user-specific authorization.
- OAuth 2.0: A robust authorization framework, not an authentication protocol itself, but often used with OpenID Connect for authentication. Delegates access to third-party applications without sharing user credentials.
- Token-Based Authentication (e.g., JWT): After initial login, the server issues a signed token (JWT). The client includes this token in subsequent requests, and the server validates it. This is stateless and scalable.
GET /api/v1/users/123
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Example of a request with a JWT in the Authorization header