Connecting to RDS Postgres from remote machine
Categories:
Connecting to AWS RDS PostgreSQL from a Remote Machine
Learn how to securely establish a connection to your Amazon RDS PostgreSQL instance from a remote client, covering security groups, user authentication, and common troubleshooting steps.
Connecting to an Amazon Relational Database Service (RDS) PostgreSQL instance from a remote machine is a common task for developers and administrators. While AWS provides a robust and secure environment, proper configuration is essential to ensure both accessibility and data protection. This article will guide you through the necessary steps, focusing on network configuration, user authentication, and best practices for a secure connection.
Understanding AWS RDS Network Configuration
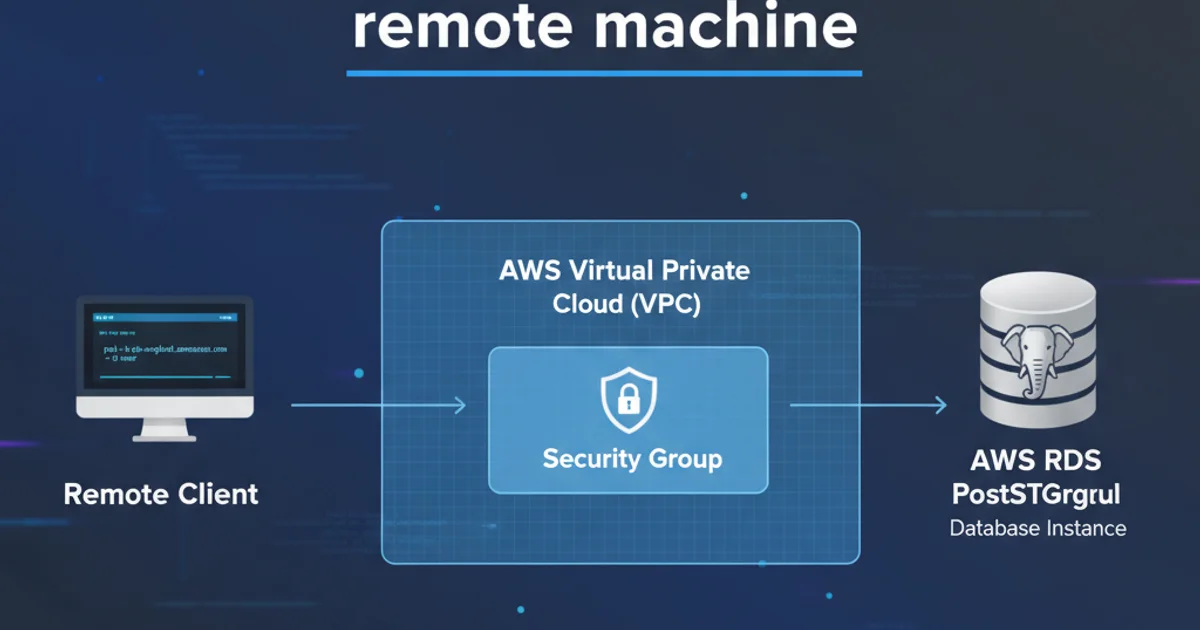
Before attempting to connect, it's crucial to understand how AWS RDS instances are typically deployed and secured within the AWS ecosystem. RDS instances reside within a Virtual Private Cloud (VPC), which acts as a virtual network dedicated to your AWS account. Access to this VPC, and subsequently to your RDS instance, is controlled by security groups and network ACLs.
flowchart TD
A[Remote Client] --> B["Internet (Public IP)"]
B --> C["AWS VPC (Public Subnet)"]
C --> D["Security Group (Inbound Rule: Port 5432)"]
D --> E["RDS PostgreSQL Instance"]
E -- "Requires: DB User & Password" --> AConceptual flow for connecting to AWS RDS PostgreSQL from a remote client.
Step-by-Step Connection Guide
Follow these steps to configure your AWS RDS PostgreSQL instance and your remote machine for a successful connection.
1. 1. Identify Your Remote Machine's Public IP Address
Your remote machine (the one you're connecting from) needs its public IP address to be whitelisted in the RDS security group. You can find this by searching "What is my IP?" on Google or using a service like ifconfig.me.
2. 2. Configure AWS RDS Security Group
Navigate to the Amazon RDS console, select your PostgreSQL instance, and then click on the 'Connectivity & security' tab. Under 'Security', click on the active VPC security group. Add an inbound rule:
- Type: PostgreSQL
- Protocol: TCP
- Port range: 5432
- Source: Custom (and enter your remote machine's public IP address with a
/32CIDR suffix, e.g.,192.0.2.1/32). Alternatively, for testing, you can use0.0.0.0/0(all IPs), but this is highly discouraged for production environments.
3. 3. Obtain RDS Endpoint and Port
From the RDS console, on your instance's 'Connectivity & security' tab, note down the 'Endpoint' and 'Port' (default is 5432). These are essential for your connection string.
4. 4. Install PostgreSQL Client (psql)
If you don't already have a PostgreSQL client installed on your remote machine, you'll need one. psql is the command-line client that comes with PostgreSQL. For macOS, you can use Homebrew: brew install postgresql. For Debian/Ubuntu: sudo apt-get install postgresql-client.
5. 5. Connect Using psql
Open your terminal or command prompt and use the psql command with the endpoint, port, database name, and username. You will be prompted for the password.
psql -h <RDS_ENDPOINT> -p 5432 -U <DB_USERNAME> -d <DB_NAME>
Example psql command to connect to your RDS instance.
Troubleshooting Common Connection Issues
If you encounter problems connecting, consider the following common issues:
- Security Group Misconfiguration: This is the most frequent cause. Double-check that your remote machine's public IP address is correctly whitelisted in the RDS instance's security group for port 5432.
- Incorrect Endpoint or Port: Verify the endpoint and port from the RDS console. Typos are common.
- Incorrect Credentials: Ensure the username and password are correct. Remember that the master username for RDS is not necessarily
postgres. - Database Not Found: Confirm the database name you are trying to connect to exists on the RDS instance.
- Network ACLs: While less common for basic connections, if you have custom Network ACLs configured on your VPC subnets, ensure they also allow inbound and outbound traffic on port 5432.
- Public Accessibility: Ensure your RDS instance is publicly accessible if you intend to connect from the internet. This setting is configured during instance creation or modification under 'Connectivity & security'.
graph TD
A[Connection Fails?] --> B{Check Security Group Inbound Rules}
B -- No Access --> C[Add Remote IP to SG for Port 5432]
B -- Access OK --> D{Verify RDS Endpoint & Port}
D -- Incorrect --> E[Update Connection String]
D -- Correct --> F{Check DB Username & Password}
F -- Incorrect --> G[Reset/Verify Credentials]
F -- Correct --> H{Is RDS Publicly Accessible?}
H -- No --> I[Modify RDS Instance to be Publicly Accessible]
H -- Yes --> J[Review Network ACLs / Other Network Issues]
C --> K[Retry Connection]
E --> K
G --> K
I --> K
J --> KTroubleshooting flowchart for RDS PostgreSQL connection issues.